Jan 11, 2024NewsroomVulnerability / Cyber Attack Cybersecurity researchers have developed a proof-of-concept (PoC) code that exploits a recently disclosed critical flaw in the Apache OfBiz open-source Enterprise Resource Planning (ERP) system to execute a memory-resident payload. The vulnerability in question is CVE-2023-51467 (CVSS score: 9.8), a bypass for another severe shortcoming in the same software […]
Governance & Risk Management , IT Risk Management Cyber Regulation Requires EU Agencies to Assess Risks and Report Incidents Akshaya Asokan (asokan_akshaya) • January 10, 2024 The European Union adopted a regulation intended to strengthen institutional cybersecurity. (Image: Shutterstock) The European Union adopted a regulation on mandatory cyber hygiene intended to beef up […]
The first vulnerability enables an attacker to reset the API key and access sensitive log information, while the second vulnerability allows for arbitrary script injection into affected web pages.
A team of computer scientists led by the University of Massachusetts Amherst recently announced a new method for automatically generating whole proofs that can be used to prevent software bugs and verify that the underlying code is correct. This new method, called Baldur, leverages the artificial intelligence power of LLMs, and, when combined with the […]
Takedown of malware infrastructure by law enforcement has proven to have an impact, albeit limited, on cybercriminal activity, according to threat intelligence provider Recorded Future. In its 2023 Adversary Infrastructure Report, published on January 9, 2024, Recorded Future analyzed the effect of three malware takedown operations that took place in 2023 or before: The Emotet […]
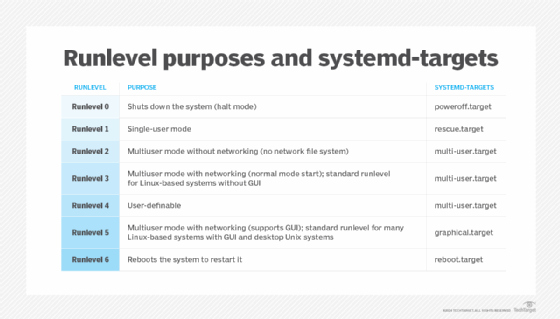
What is a runlevel? A runlevel is an operating state on a Unix and Unix-based operating system (OS) that is preset on the Linux-based system. Runlevels are numbered from zero to six and play several important roles in the operations, maintenance and management of Linux and Unix systems. A runlevel is a preset operating state, […]
Last updated 16 January, 2024 Device Library Plus is a new database that as of now gets added to your USB stick or SD card whenever you export playlists from Rekordbox to DJ with, alongside the music files. In this article (and accompanying video), I’ll explain what it is, why it’s there, what you should […]
Wes warms up for BMW24 Wigan-born Wes Baggaley has played everywhere from legendary queer night Adonis to Berlin’s Berghain, as well as one half of the excellent party stoking duo Bottom Heavy. As well as very kindly taking to the decks to spin out an hour of the best house, techno, garage and disco for […]
The NCSC-FI has warned of increased Akira ransomware attacks in December. These attacks targeted companies in Finland and involved wiping backups, making it difficult for victims to recover their data without paying a ransom.