Picture a cybersecurity landscape where defenses are impenetrable, and threats are nothing more than mere disturbances deflected by a strong shield. Sadly, this image of fortitude remains a pipe dream despite its comforting nature. In the security world, preparedness is not just a luxury but a necessity. In this context, Mike Tyson’s famous adage, “Everyone […]
Jan 12, 2024NewsroomDevSecOps / Software security GitLab has released security updates to address two critical vulnerabilities, including one that could be exploited to take over accounts without requiring any user interaction. Tracked as CVE-2023-7028, the flaw has been awarded the maximum severity of 10.0 on the CVSS scoring system and could facilitate account takeover by […]
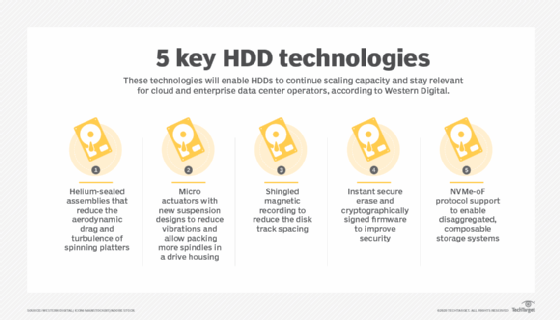
What is shingled magnetic recording (SMR)? Shingled magnetic recording (SMR) is a technique for writing data to a hard disk drive (HDD) whereby the data tracks partially overlap to increase the areal density and overall storage capacity per disk. In SMR HDDs, the term derives from the manner in which shingles are installed on a […]
The leaked data, containing names, phone numbers, and addresses, appears to be accurate according to users listed in the file. Customers should be cautious of potential smishing attacks and the misuse of their information for fraudulent purposes.
Merck & Co.’s proposed settlement with insurers over a $1.4 billion claim related to the NotPetya attack will change the language the insurance industry uses to exclude acts of war in its policies, and organizations need to consider how those changes affect risk, said attorney Peter Halprin. The settlement will resolve an ongoing legal dispute […]
The latest World Economic Forum Global Risks Report 2024 highlighted the rising tide of cyber threats and places misinformation and disinformation as the most severe risk globally. It also warned of low-cost crime havens and issues surrounding concentrated AI power in few hands. Misinformation and Undermining Truth Misinformation and disinformation have emerged as the most […]
The breach occurred when a threat actor impersonated Framework’s CEO and tricked an accountant into sharing a spreadsheet containing customer data, including names, email addresses, and outstanding balances.
Jan 12, 2024NewsroomCryptocurrency / Malware Cybersecurity researchers have identified a new attack that exploits misconfigurations in Apache Hadoop and Flink to deploy cryptocurrency miners within targeted environments. “This attack is particularly intriguing due to the attacker’s use of packers and rootkits to conceal the malware,” Aqua security researchers Nitzan Yaakov and Assaf Morag said in […]
This month’s best new modules include TipTop’s latest Buchla reissue, a unique quad envelope from Eowave and serious audio seasoning from Frap Tools. Buchla & TipTop Audio Model 296t TipTop Audio’s officially licensed Buchla modules have been some of our favourites over the last year. Bringing the iconic Buchla modules to a more accessible, Eurorack-compatible […]