A new ransomware group called Alpha has recently emerged with the launch of its Dedicated/Data Leak Site (DLS) on the Dark Web, featuring an initial listing of data from six victims. Despite its recent appearance, Alpha ransomware (distinct from ALPH) has been observed since May 2023, with a lower infection rate compared to its competitors […]
Jan 31, 2024NewsroomVulnerability / Endpoint Security Malicious local attackers can obtain full root access on Linux machines by taking advantage of a newly disclosed security flaw in the GNU C library (aka glibc). Tracked as CVE-2023-6246, the heap-based buffer overflow vulnerability is rooted in glibc’s __vsyslog_internal() function, which is used by syslog() and vsyslog() for […]
Jan 31, 2024NewsroomCyber Attack / Network Security A pair of recently disclosed zero-day flaws in Ivanti Connect Secure (ICS) virtual private network (VPN) devices have been exploited to deliver a Rust-based payload called KrustyLoader that’s used to drop the open-source Sliver adversary simulation tool. The security vulnerabilities, tracked as CVE-2023-46805 (CVSS score: 8.2) and CVE-2024-21887 […]
Jan 30, 2024NewsroomDevSecOps / Vulnerability GitLab once again released fixes to address a critical security flaw in its Community Edition (CE) and Enterprise Edition (EE) that could be exploited to write arbitrary files while creating a workspace. Tracked as CVE-2024-0402, the vulnerability has a CVSS score of 9.9 out of a maximum of 10. “An […]
Some 33,000 small and medium-size businesses in Israel experienced some form of cyberattack last year, with 7,000 suffering major damage. New data from the Small and Medium Business Agency at the Israeli Ministry of Economy and Industry shows that 5% of surveyed businesses reported they had suffered some form of cyberattack. The smallest businesses — […]
Enlarge Getty Images OpenAI officials say that the ChatGPT histories a user reported result from his ChatGPT account being compromised. The unauthorized logins came from Sri Lanka, an Open AI representative said. The user said he logs into his account from Brooklyn, New York. “From what we discovered, we consider it an account take over […]
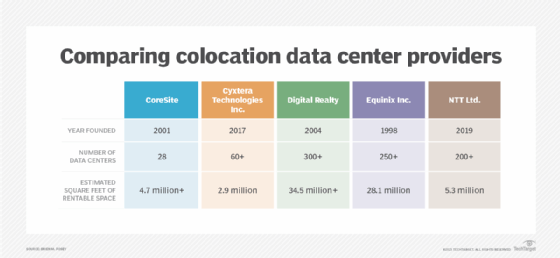
There’s a growing demand for third-party, on-premises data centers that enable organizations to reduce or eliminate expenses related to managing power, connectivity, space and cooling. However, selecting a data center to host an organization’s equipment is not easy, as there are numerous colocation providers that offer a multitude of services and contracts. What is colocation? […]
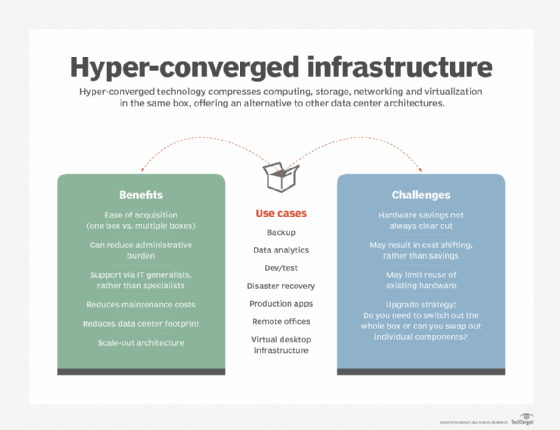
Hyper-converged infrastructure technology has taken big strides since emerging more than a decade ago, finding a home in data centers looking to ease procurement headaches and management chores. Vendors originally positioned the technology as a simple-to-deploy, all-in-one offering that combined compute, storage and networking with a hypervisor. The essential selling points around simplicity remain the […]
There’s a growing demand for third-party, on-premises data centers that enable organizations to reduce or eliminate expenses related to managing power, connectivity, space and cooling. However, selecting a data center to host an organization’s equipment is not easy, as there are numerous colocation providers that offer a multitude of services and contracts. What is colocation? […]