XProtect, macOS’s built-in anti-malware system, struggles to detect evolving info-stealers like KeySteal and Atomic Stealer, highlighting the need for more robust security measures.
Developer-focused security company Snyk said it has acquired Helios, a startup focused on helping developers troubleshoot applications in runtime and production. The acquisition enhances Snyk’s “cloud-to-code risk visibility” by combining Helios’ full-stack runtime data collection and insights with the Snyk Developer Security Platform, Snyk said in a statement. While security testing, such as static analysis […]
A cryptocurrency trading company has shut down after agreeing to pay an $8 million penalty and surrender its licenses to New York state regulators, who found it had violated multiple financial industry rules, including cybersecurity protections. Genesis Global Trading, Inc. had “compliance failures” that “left the company vulnerable to illicit activity and cybersecurity threats,” including […]
Citrix warns admins to immediately patch NetScaler for actively exploited zero-days Pierluigi Paganini January 17, 2024 Citrix fixed two actively exploited zero-day vulnerabilities impacting Netscaler ADC and Gateway appliances. Citrix warns customers to install security updates to address two actively exploited zero-day vulnerabilities, tracked as CVE-2023-6548 and CVE-2023-6549, impacting Netscaler ADC and Gateway appliances. “Exploits […]
Jan 17, 2024NewsroomFinancial Data / Vulnerability The point-of-sale (PoS) terminals from PAX Technology are impacted by a collection of high-severity vulnerabilities that can be weaponized by threat actors to execute arbitrary code. The STM Cyber R&D team, which reverse engineered the Android-based devices manufactured by the Chinese firm owing to their rapid deployment in Poland, […]
Wing Security announced today that it now offers free discovery and a paid tier for automated control over thousands of AI and AI-powered SaaS applications. This will allow companies to better protect their intellectual property (IP) and data against the growing and evolving risks of AI usage. SaaS applications seem to be multiplying by the […]
Toolroom Records also to release fundraising single Fans of celebrated house music vocalist Kathy Brown are rallying round the singer after catastrophic medical news. Late last year Brown, who has sung on records by artists as varied as David Morales and J Majik, was was diagnosed with stage four lung cancer, which has now spread […]
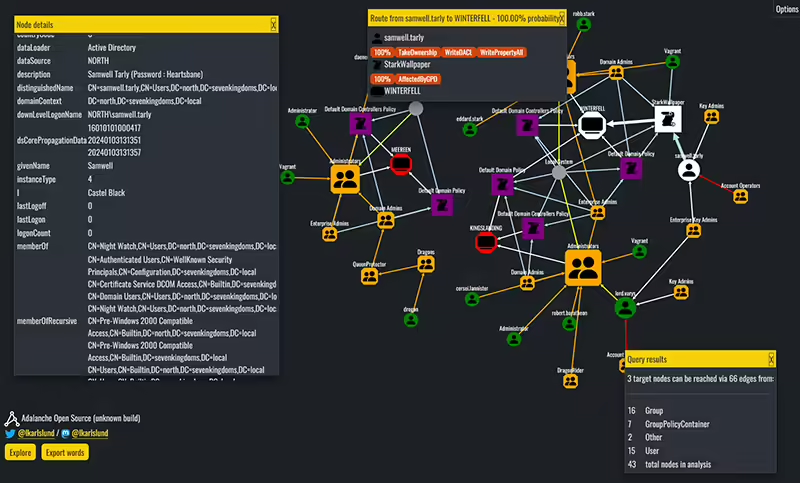
Adalanche provides immediate insights into the permissions of users and groups within an Active Directory. It’s an effective open-source tool for visualizing and investigating potential account, machine, or domain takeovers. Additionally, it helps identify and display any misconfigurations. What unique features make Adalanche stand out? “The best feature is the low user effort to get […]
The flaws affect Tianocore’s EDK II UEFI implementation and other major tech companies and BIOS providers, prompting a coordinated disclosure effort by CERT/CC and CERT-FR.