Jan 17, 2024NewsroomVulnerability / Cyber Threat Citrix is warning of two zero-day security vulnerabilities in NetScaler ADC (formerly Citrix ADC) and NetScaler Gateway (formerly Citrix Gateway) that are being actively exploited in the wild. The flaws are listed below – CVE-2023-6548 (CVSS score: 5.5) – Authenticated (low privileged) remote code execution on Management Interface (requires […]
Jan 17, 2024NewsroomBrowser Security / Vulnerability Google on Tuesday released updates to fix four security issues in its Chrome browser, including an actively exploited zero-day flaw. The issue, tracked as CVE-2024-0519, concerns an out-of-bounds memory access in the V8 JavaScript and WebAssembly engine, which can be weaponized by threat actors to trigger a crash. “By […]
Last updated 16 January, 2024 It’s a new year, but some of the old frustrations are still there in the DJ world for both hobby and working DJs. And of course, we’re always all dreaming about other improvements we’d like to see in our DJ gear, software, and systems in an ideal world. So as […]
Last updated 16 January, 2024 Every year here at the Digital DJ Tips school we conduct the Global DJ Census, giving DJs the chance to let the industry know what they want, where they’re at, what their concerns are, and a whole lot more. As ever, it’s been very popular this year with 15,000 people […]
The U.S. Secret Service executed a seizure warrant to recover $34,000 stolen through a fake Norton antivirus renewal email scam. The scam tricked victims into granting remote access to their computers, and then transferring money from their accounts.
Jan 16, 2024NewsroomVulnerability / Network Security Over 178,000 SonicWall firewalls exposed over the internet are exploitable to at least one of the two security flaws that could be potentially exploited to cause a denial-of-service (DoS) condition and remote code execution (RCE). “The two issues are fundamentally the same but exploitable at different HTTP URI paths […]
Jan 16, 2024The Hacker NewsData Security / Privacy Compliance Explore how an advanced exposure management solution saved a major retail industry client from ending up on the naughty step due to a misconfiguration in its cookie management policy. This wasn’t anything malicious, but with modern web environments being so complex, mistakes can happen, and non-compliance […]
Attackers can exploit these vulnerabilities to force affected firewalls into maintenance mode, impacting their standard functionality and VPN access to corporate networks.
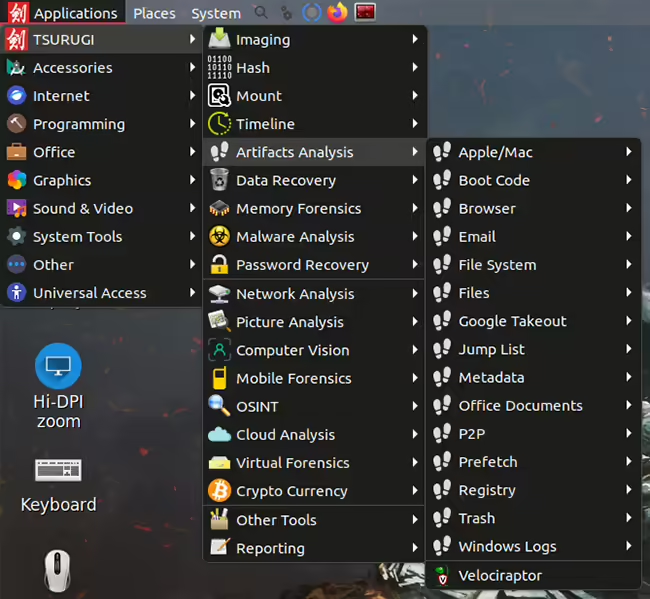
Tsurugi Linux is a heavily customized open-source distribution focused on supporting DFIR investigations. The project focuses mainly on live forensics analysis, post-mortem analysis, and digital evidence acquisition. Users can also perform malware analysis, OSINT and computer vision activities. “We’ve crafted a user-friendly experience, organizing the main menu in a logical forensic analysis sequence. Our menu […]
- 1
- 2