The first vulnerability enables an attacker to reset the API key and access sensitive log information, while the second vulnerability allows for arbitrary script injection into affected web pages.
A team of computer scientists led by the University of Massachusetts Amherst recently announced a new method for automatically generating whole proofs that can be used to prevent software bugs and verify that the underlying code is correct. This new method, called Baldur, leverages the artificial intelligence power of LLMs, and, when combined with the […]
Takedown of malware infrastructure by law enforcement has proven to have an impact, albeit limited, on cybercriminal activity, according to threat intelligence provider Recorded Future. In its 2023 Adversary Infrastructure Report, published on January 9, 2024, Recorded Future analyzed the effect of three malware takedown operations that took place in 2023 or before: The Emotet […]
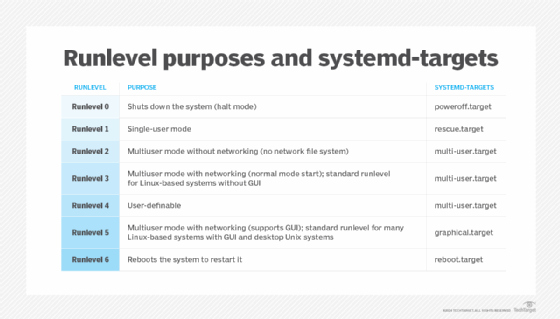
What is a runlevel? A runlevel is an operating state on a Unix and Unix-based operating system (OS) that is preset on the Linux-based system. Runlevels are numbered from zero to six and play several important roles in the operations, maintenance and management of Linux and Unix systems. A runlevel is a preset operating state, […]