Jan 10, 2024NewsroomVulnerability / Windows Security Microsoft has addressed a total of 48 security flaws spanning its software as part of its Patch Tuesday updates for January 2024. Of the 48 bugs, two are rated Critical and 46 are rated Important in severity. There is no evidence that any of the issues are publicly known […]
Jan 10, 2024NewsroomPatch Management / Threat Intelligence The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added six security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. This includes CVE-2023-27524 (CVSS score: 8.9), a high-severity vulnerability impacting the Apache Superset open-source data visualization software that could enable remote code execution. […]
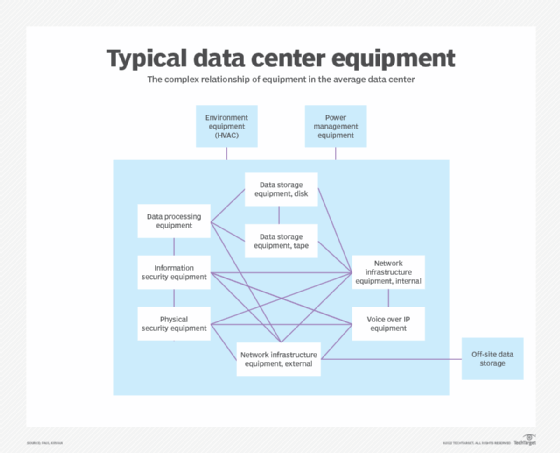
The data center market continues to evolve, with the level of critical infrastructure requiring that data center infrastructure management software evolves with it. DCIM tools are now a necessity for most data centers, as managing complex computing operations — often with far-flung segments — can quickly overload the human ability to process. The DCIM industry […]
Sheer genius The news that perennial DIY punk popsters Sheer Mag had signed to the White Stripes-affiliated Third Man label last year signified that the band would be stepping up a gear, and quite poosibly changing creative tack too. But the tracks that the US band has managed to flaunt ahead of their forthcoming next […]
Last updated 10 January, 2024 Now is a great time to commit to improving your DJing this year. Often we reach plateaus. And if we’re not careful, the years slip by, and we’re not registering any real improvements in our DJing. What I’m going to share with you now is a simple five-step plan for […]
Jan 09, 2024NewsroomData Security / Cyber Attack Poorly secured Microsoft SQL (MS SQL) servers are being targeted in the U.S., European Union, and Latin American (LATAM) regions as part of an ongoing financially motivated campaign to gain initial access. “The analyzed threat campaign appears to end in one of two ways, either the selling of […]
Jan 09, 2024NewsroomMalware / Cyber Threat A threat actor called Water Curupira has been observed actively distributing the PikaBot loader malware as part of spam campaigns in 2023. “PikaBot’s operators ran phishing campaigns, targeting victims via its two components — a loader and a core module — which enabled unauthorized remote access and allowed the […]
Cisco Talos obtained executable code capable of decrypting files affected by the Babuk Tortilla ransomware variant, allowing Talos to extract and share the private decryption key used by the threat actor. Cisco Talos shared the key with our peers at Avast for inclusion in the Avast Babuk decryptor released in 2021. The decryptor includes all […]
Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Agency Prepares $1.7M Contracts for Synthetic Data Prototypes Rashmi Ramesh (rashmiramesh_) • January 8, 2024 The U.S. federal government is preparing for an era of synthetic data. (Image: Shutterstock) In a solicitation for synthetic data generators, the U.S. federal government is looking […]