LastPass, a popular password management solution, is now requiring customers to use complex master passwords with a minimum of 12 characters to enhance account security. Previously, users had the option to use weaker passwords.
The hacker changed the AS number associated with Orange Spain’s IP addresses and enabled an invalid RPKI configuration, causing the IP addresses to no longer be announced properly.
Jan 04, 2024NewsroomCryptocurrency Miner / Malware Three new malicious packages have been discovered in the Python Package Index (PyPI) open-source repository with capabilities to deploy a cryptocurrency miner on affected Linux devices. The three harmful packages, named modularseven, driftme, and catme, attracted a total of 431 downloads over the past month before they were taken […]
The Federal Trade Commission (FTC) is now accepting submissions for a contest designed to spur development of products and policies to protect consumers from the malicious use of voice cloning technology, which has been fueled by the advance of text-to-speech artificial intelligence capabilities. The challenge is an effort by the FTC to speed the evolution […]
In 2023, businesses have been hit with 800,000 cyberattacks, over 60,000 of which were DDoS attacks and 4,000 falling victim to ransomware, according to Vercara. The research found that consumers hold nuanced perceptions regarding cybersecurity incidents and are often less aware of the role they play in maintaining cyber hygiene within a business. These findings […]
Ukraine’s security officers said they took down two online surveillance cameras that were allegedly hacked by Russia to spy on air defense forces and critical infrastructure in Ukraine’s capital, Kyiv. The cameras were installed on residential buildings in Kyiv and were initially used by residents to monitor the surrounding area and parking lot. After hacking […]
The fraud scheme involved unauthorized access to email accounts, impersonating employees, and tricking one charity into transferring funds to accounts controlled by the attacker.
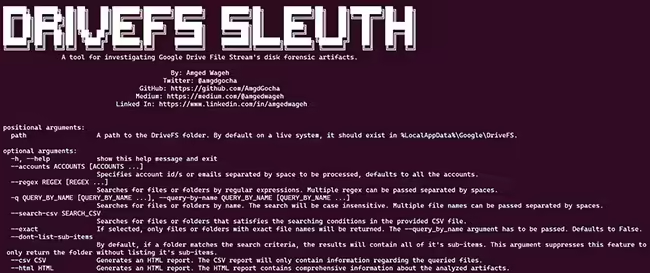
DriveFS Sleuth automates the investigation of Google Drive File Stream disk artifacts. The tool can parse the disk artifacts and build a filesystem tree-like structure enumerating the synchronized files along with their respective properties. “While engaged in a threat-hunting activity for a client to detect the misuse of file-syncing applications within their network, I identified […]
Airbus is expected to offer between €1.5 to 1.8 billion (~$1.64 to 1.97 billion) for Atos’ Big Data & Security division, in line with its goal of growing its cybersecurity arm and enhancing its defense and security portfolio.