Concept paper highlights ongoing and planned steps to improve cyber resiliency and protect patient safety. WASHINGTON – The U.S. Department of Health and Human Services (HHS) today released a concept paper that outlines the Department’s cybersecurity strategy for the health care sector. The concept paper builds on the National Cybersecurity Strategy that President Biden released […]
Dec 11, 2023NewsroomEndpoint Security / Malware A new collection of eight process injection techniques, collectively dubbed PoolParty, could be exploited to achieve code execution in Windows systems while evading endpoint detection and response (EDR) systems. SafeBreach researcher Alon Leviev said the methods are “capable of working across all processes without any limitations, making them more […]
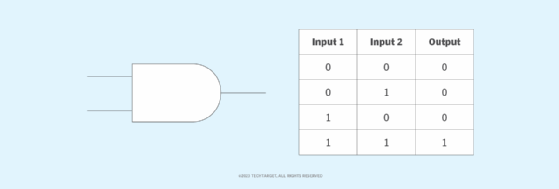
What is a logic gate? A logic gate is a device that acts as a building block for digital circuits. They perform basic logical functions that are fundamental to digital circuits. Most electronic devices we use today will have some form of logic gates in them. For example, logic gates can be used in digital […]
Dec 09, 2023NewsroomCyber Threat / Hardware Security Researchers from the Vrije Universiteit Amsterdam have disclosed a new side-channel attack called SLAM that could be exploited to leak sensitive information from kernel memory on current and upcoming CPUs from Intel, AMD, and Arm. The attack is an end-to-end exploit for Spectre based on a new feature […]
AI security researchers from Robust Intelligence and Yale University have designed a machine learning technique that can speedily jailbreak large language models (LLMs) in an automated fashion. “The method, known as the Tree of Attacks with Pruning (TAP), can be used to induce sophisticated models like GPT-4 and Llama-2 to produce hundreds of toxic, harmful, […]
Bypassing major EDRs using Pool Party process injection techniques Pierluigi Paganini December 08, 2023 Researchers devised a novel attack vector for process injection, dubbed Pool Party, that evades EDR solutions. Researchers from cybersecurity firm SafeBreach devised a set of process injection techniques, dubbed Pool Party, that allows bypassing EDR solutions. They presented the technique at Black […]
The organization that runs the transit system for central Virginia dealt with a computer network disruption due to a cyberattack around the Thanksgiving holiday. The Greater Richmond Transit Company (GRTC) provides bus and specialized transportation services for millions of people across Richmond, Chesterfield and Henrico Counties. A spokesperson told Recorded Future News that around Thanksgiving […]
Dec 09, 2023NewsroomMalware / Cyberattack Threat hunters have unmasked the latest tricks adopted by a malware strain called GuLoader in an effort to make analysis more challenging. “While GuLoader’s core functionality hasn’t changed drastically over the past few years, these constant updates in their obfuscation techniques make analyzing GuLoader a time-consuming and resource-intensive process,” Elastic […]
Cybercriminals caused upheaval for 180 homeowners on a private group water scheme in the Erris area last week as their equipment was targeted in a politically motivated cyber-attack. Residents on the Binghamstown/Drum scheme were without their water supply on Thursday and Friday after the extraordinary incident as crews worked to repair the Eurotronics Israeli-made water […]