Nansen stopped the malicious activity shortly after the affected vendor informed them about the incident, but the ensuing investigation confirmed that user data was compromised.
Despite the sophisticated techniques used, users can still protect themselves by being cautious of unsolicited links, suspicious messages, and checking URLs for deception, as well as contacting the company directly for clarification.
‘Stranger Things’ man setting New Standards AURAGRAPH is an experimental audio/visual synth-based recording project by Texas born Hector Carlos Ramirez. Currently based in Los Angeles, California, Carlos played in several bands within the punk scene in Laredo, Texas before a move to Austin, Texas prompted his fascination with synths, samplers and visual art. Carlos has score […]
Threat actors are targeting hundreds of banking customers in Latin America with a new variant of an existing banking Trojan that replicates the interfaces of more than 40 Mexican and Brazilian banks. The campaign is aimed at tricking infected victims into giving up two-factor authentication (2FA) and/or payment-card details so attackers can hijack their bank […]
Sep 22, 2023THNMalware / Cyber Threat An active malware campaign targeting Latin America is dispensing a new variant of a banking trojan called BBTok, particularly users in Brazil and Mexico. “The BBTok banker has a dedicated functionality that replicates the interfaces of more than 40 Mexican and Brazilian banks, and tricks the victims into entering […]
Fraud Management & Cybercrime , Government , Healthcare Researchers Say Breach Illustrates Why Schools Are Major Targets for Cybercriminals Marianne Kolbasuk McGee (HealthInfoSec) • September 21, 2023 Image: Lakeland Community College An Ohio community college is notifying 290,000 people of a data theft breach this spring that may have compromised their personal, financial […]
Key Points A malicious Python package, “Culturestreak”, hijacks system resources for unauthorized cryptocurrency mining. The malicious package utilizes obfuscated code and random filenames to evade detection. The code runs in an infinite loop, making it a relentless threat that continually exploits system resources. The malicious code originates from an active GitLab repository, underscoring the ongoing […]
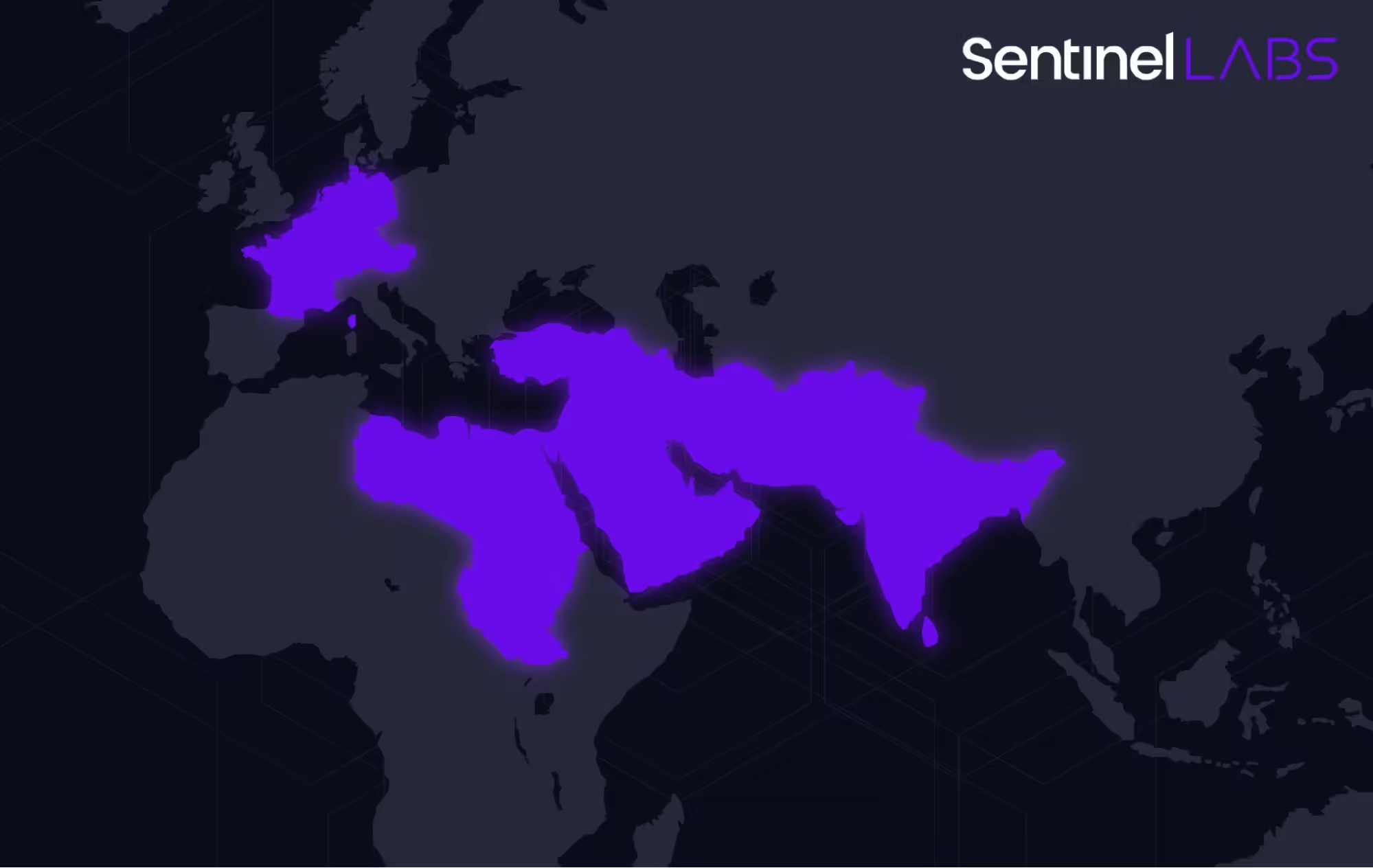
By Aleksandar Milenkoski, in collaboration with QGroup Executive Summary SentinelLabs has observed a new threat activity cluster by an unknown threat actor we have dubbed Sandman. Sandman has been primarily targeting telecommunication providers in the Middle East, Western Europe, and the South Asian subcontinent. The activities are characterized by strategic lateral movements and minimal engagements, […]
Apple released emergency security updates to patch three new zero-day vulnerabilities exploited in attacks targeting iPhone and Mac users, for a total of 16 zero-days fixed this year.