The attackers infect victims’ devices and then inject a script onto the victim’s browser to modify webpage content. This new approach makes the attacks more stealthy and harder to detect.
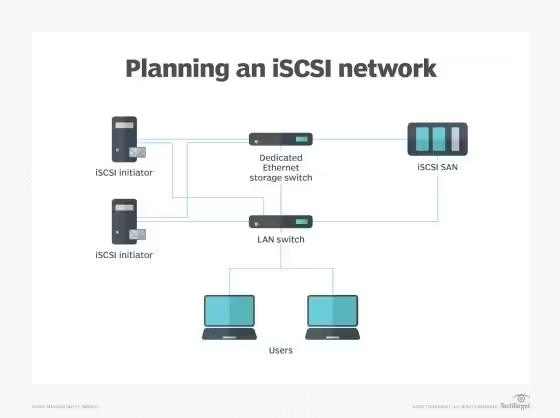
What is an iSCSI initiator? An Internet Small Computer System Interface initiator is software or hardware that lets a host computer send data to an external iSCSI-based storage array through an Ethernet network adapter over a TCP-based IP network. ISCSI is a protocol for sharing block storage and communicating with input/output (I/O) devices over a TCP/IP network. […]
Iranian espionage group Seedworm (aka Muddywater) has been targeting organizations operating in the telecommunications sector in Egypt, Sudan, and Tanzania. Seedworm has been active since at least 2017, and has targeted organizations in many countries, though it is most strongly associated with attacks on organizations in the Middle East. It has been publicly stated that […]
Both Russia and China attempted to influence the 2022 U.S. midterms but did not successfully hack into the country’s election infrastructure or otherwise disrupt voting, the U.S. intelligence community said on Monday. “We have no evidence that any detected activity prevented voting, changed votes, or disrupted the ability to tally votes or to transmit election […]
Dec 20, 2023The Hacker NewsBrandjacking / Cyber Threat Hands-On Review: Memcyco’s Threat Intelligence Solution Website impersonation, also known as brandjacking or website spoofing, has emerged as a significant threat to online businesses. Malicious actors clone legitimate websites to trick customers, leading to financial scams and data theft causing reputation damage and financial losses for both […]
An international group of law enforcement agencies has seized the dark web leak site of the notorious ransomware gang known as ALPHV, or BlackCat. “The Federal Bureau of Investigation seized this site as part of a coordinated law enforcement action taken against ALPHV Blackcat Ransomware,” a message on the gang’s dark web leak site now […]
Microsoft Excel Infection Sequence Threat actors begin the infection sequence by distributing spam emails with malicious attachments (like in Figure 1 and Figure 2 below) in hopes that users on vulnerable versions of Microsoft Excel open these emails and download the attachments. Figure 1: Spam email example Figure 2: Spam email example To make these […]
Dec 20, 2023NewsroomIdentity Theft / SMS Phishing The Chinese-speaking threat actors behind Smishing Triad have been observed masquerading as the United Arab Emirates Federal Authority for Identity and Citizenship to send malicious SMS messages with the ultimate goal of gathering sensitive information from residents and foreigners in the country. “These criminals send malicious links to […]
2023 proved to be a challenging year on the ransomware front after a brief lull in 2022. According to data from cryptocurrency tracing firm Chainalysis, victims had paid ransomware groups well over $400 million combined as of July 2023. Statista, meanwhile, reports that a whopping 72% of businesses have been affected by ransomware attacks as […]