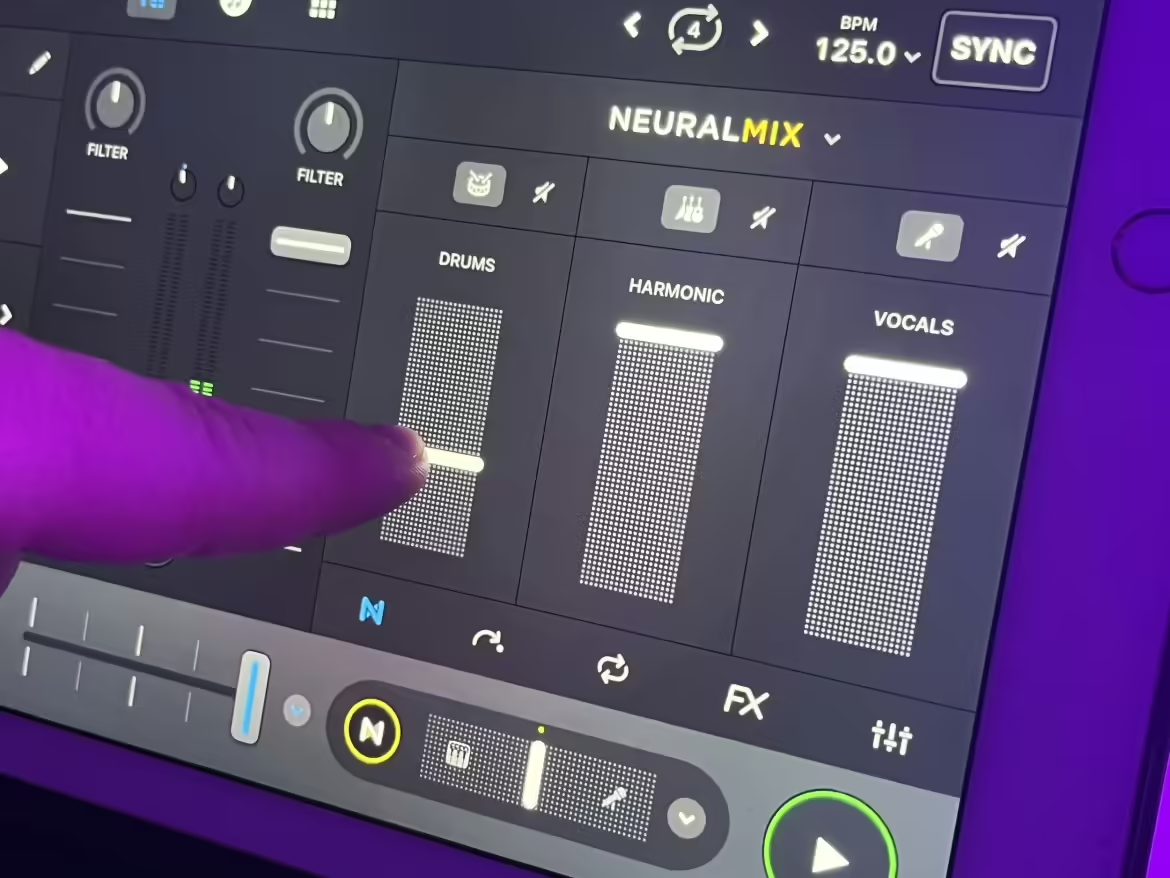
For years, one of the biggest powerhouses in the DJ software world has been Algoriddim. With their djay and djay Pro softwares, they took their Apple and iOS-centric design prowess and fed it directly into innovation and new features. They were among the first to bring real-time stem separation to DJ software while others were […]
Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Geo Focus: Asia Andariel Group Rented Server to Steal 1.2TB of Data, Extort $357,000 in Ransoms Jayant Chakravarti (@JayJay_Tech) • December 5, 2023 A Seoul Metropolitan Police Agency police station (Image Shutterstock) Seoul police have accused the North Korean hacker group Andariel of […]
Israeli startup Mine made a name for itself a few years ago with a tool designed for consumers to quickly run an audit of their data privacy situation. One scan of your inbox using AI and specifically natural language processing, and Mine can triangulate which companies have access to your personal data, and then let […]
Dec 06, 2023NewsroomAccess Management / Cloud Security Threat actors can take advantage of Amazon Web Services Security Token Service (AWS STS) as a way to infiltrate cloud accounts and conduct follow-on attacks. The service enables threat actors to impersonate user identities and roles in cloud environments, Red Canary researchers Thomas Gardner and Cody Betsworth said […]
Admins are advised to upgrade to the latest ALEOS version, change default SSL certificates, disable non-essential services, implement web application firewalls, and install an OT/IoT-aware IDS for enhanced protection against these vulnerabilities.
This research explores a scenario in which a vulnerable device is compromised by an attacker who plants the code to implement Fake Lockdown Mode. When a high-risk user (e.g., journalists, government officials, executives) of the compromised device initiates Lockdown Mode, they trigger the attacker’s code that implements the visual cues of Lockdown Mode, but makes […]
Since the beginning of 2023, ESET researchers have observed an alarming growth of deceptive Android loan apps, which present themselves as legitimate personal loan services, promising quick and easy access to funds. Despite their attractive appearance, these services are in fact designed to defraud users by offering them high-interest-rate loans endorsed with deceitful descriptions, all […]
Dec 06, 2023The Hacker NewsBrowser Security / Privacy Compromising the browser is a high-return target for adversaries. Browser extensions, which are small software modules that are added to the browser and can enhance browsing experiences, have become a popular browser attack vector. This is because they are widely adopted among users and can easily turn […]
Threat actor leveraging patched vulnerabilities to send high-volume campaigns to targets in Europe and North America