By Published: 12 Dec 2023 Server troubleshooting is a fine art, but there are some straightforward methods and tips to get things running… smoothly. ITIL methodology delves into how to troubleshoot a server or a related issue more deeply, but the general theme is to narrow down the problem as quickly and efficiently as […]
By Published: 12 Dec 2023 Server troubleshooting is a fine art, but there are some straightforward methods and tips to get things running… smoothly. ITIL methodology delves into how to troubleshoot a server or a related issue more deeply, but the general theme is to narrow down the problem as quickly and efficiently as […]
By Published: 12 Dec 2023 A server is a computer intended to process centralized enterprise-class applications and communicate within a busy… business network. Although any computer can function as a server, computers that are designed and built as servers typically provide high-end computing resources, including the fastest processors, extensive amounts of fast memory, local disk […]
Greece is establishing a national cybersecurity organization to combat hackers and ransomware gangs that target governments, state institutions, utilities, schools, hospitals, and companies. It is said that a proposal for establishing a National Cybersecurity Authority to safeguard public sector and private enterprises in industries like manufacturing, chemical distribution, and food items is being sent to […]
Dec 12, 2023NewsroomZero Day / Vulnerability Apple on Monday released security patches for iOS, iPadOS, macOS, tvOS, watchOS, and Safari web browser to address multiple security flaws, in addition to backporting fixes for two recently disclosed zero-days to older devices. This includes updates for 12 security vulnerabilities in iOS and iPadOS spanning AVEVideoEncoder, ExtensionKit, Find […]
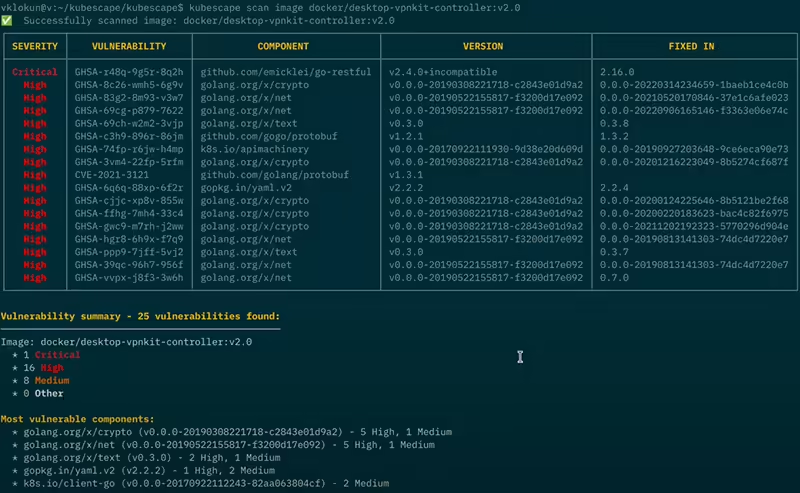
With its innovative feature for generating reliable Vulnerability Exploitability eXchange (VEX) documents, Kubescape became the first open-source project to provide this functionality. This advancement offers security practitioners a powerful tool to effectively prioritize and address software vulnerabilities. What is Vulnerability Exploitability eXchange (VEX)? Vulnerability Exploitability eXchange (VEX) is a standard that facilitates the sharing and […]
The U.S. Department of Health and Human Services (HHS) agreed to a settlement of $480,000 with Louisiana-based medical group Lafourche Medical Group following a 2021 cyberattack that exposed the sensitive information of nearly 35,000 people. In addition to the monetary penalty, the company agreed to undergo periodic audits by HHS for two years. HHS noted […]
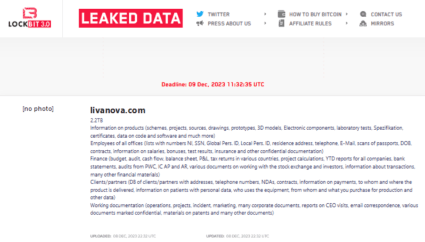
LivaNova PLC, a prominent US-based healthcare device manufacturer specializing in neuromodulation devices and cardiopulmonary products, has allegedly fallen victim to a malicious cyberattack orchestrated by the notorious LockBit ransomware group. The LivaNova data breach attack was detected on December 9, 2023, and the information was made public on the same day. LockBit ransomware group, a […]
Dec 12, 2023NewsroomVulnerability / Software Security Apache has released a security advisory warning of a critical security flaw in the Struts 2 open-source web application framework that could result in remote code execution. Tracked as CVE-2023-50164, the vulnerability is rooted in a flawed “file upload logic” that could enable unauthorized path traversal and could be […]