Dec 28, 2023NewsroomCloud Security / Data Protection Google Cloud has addressed a medium-severity security flaw in its platform that could be abused by an attacker who already has access to a Kubernetes cluster to escalate their privileges. “An attacker who has compromised the Fluent Bit logging container could combine that access with high privileges required […]
The Albanian parliament and a telecom company operating in the country were targeted by cyberattacks this week, the country’s cyber agency said in a statement. According to the agency, the attacks originated from outside Albania and country’s tech experts “are currently working to recover the affected systems and analyze the tactics and techniques used by […]
Dec 28, 2023NewsroomSpyware / Hardware Security The Operation Triangulation spyware attacks targeting Apple iOS devices leveraged never-before-seen exploits that made it possible to even bypass pivotal hardware-based security protections erected by the company. Russian cybersecurity firm Kaspersky, which discovered the campaign at the beginning of 2023 after becoming one of the targets, described it as […]
The newly surfaced DragonForce ransomware gang has claimed responsibility for the attack, stating that they have encrypted devices and stolen data, including personal information of Ohio Lottery customers and employees.
Enlarge Tero Vesalainen Researchers on Wednesday presented intriguing new findings surrounding an attack that over four years backdoored dozens if not thousands of iPhones, many of which belonged to employees of Moscow-based security firm Kaspersky. Chief among the discoveries: the unknown attackers were able to achieve an unprecedented level of access by exploiting a vulnerability […]
Notable security breaches have bypassed MFA to compromise taxi broker Uber, games company EA, and authentication business Okta, according to SE Labs. CISOs must bolster MFA protections SE Labs advised CISOs to step-up their efforts against attacks on systems protected by MFA in response to increased attacker activity to exploit failure points. As is often […]
The breached information includes names, contact details, dates of birth, medical and health insurance information, financial account numbers, employment status, and government identifiers.
Cybersecurity is awash in threat detection and mitigation solutions: SIEM, DLP, SOAR, MDR, EDR, XDR, and more. Threat detection is essential, as it serves to locate and minimize the threat as quickly and effectively as possible. However, some companies are starting to embrace an earlier line of defense that Gartner calls human-centric security. The tech […]
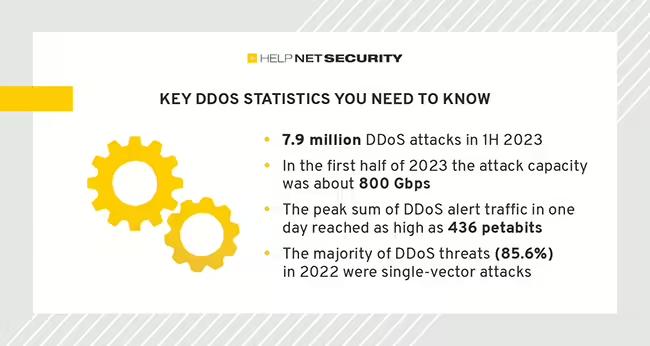
The impact of DDoS attacks extends far beyond mere inconvenience, as they can result in financial losses, compromised data, and erosion of customer trust. Understanding the nature and consequences of DDoS activity is essential for organizations and individuals alike as they strive to protect their online presence and ensure the uninterrupted flow of critical services. […]