The breached information includes names, contact details, dates of birth, medical and health insurance information, financial account numbers, employment status, and government identifiers.
Cybersecurity is awash in threat detection and mitigation solutions: SIEM, DLP, SOAR, MDR, EDR, XDR, and more. Threat detection is essential, as it serves to locate and minimize the threat as quickly and effectively as possible. However, some companies are starting to embrace an earlier line of defense that Gartner calls human-centric security. The tech […]
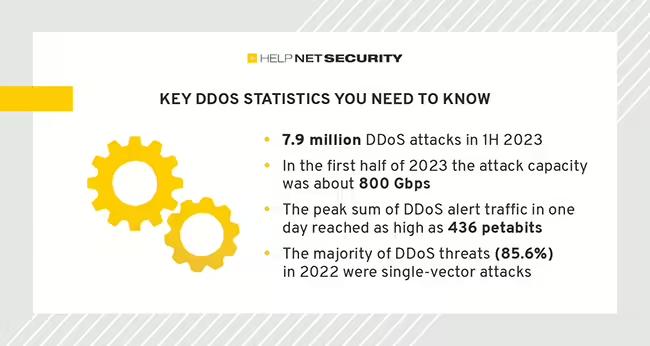
The impact of DDoS attacks extends far beyond mere inconvenience, as they can result in financial losses, compromised data, and erosion of customer trust. Understanding the nature and consequences of DDoS activity is essential for organizations and individuals alike as they strive to protect their online presence and ensure the uninterrupted flow of critical services. […]
- 1
- 2