On December 20, 2023, Rosvodokanal, the Russian water utility firm, experienced a alleged cyberattack perpetrated by the Ukrainian hacker group Blackjack. Multiple undisclosed law enforcement sources confirmed the occurrence of a cyberattack on the IT infrastructure of the Russian water utility. The announcement of the Russian water utility cyberattack was followed by the cyberattack against […]
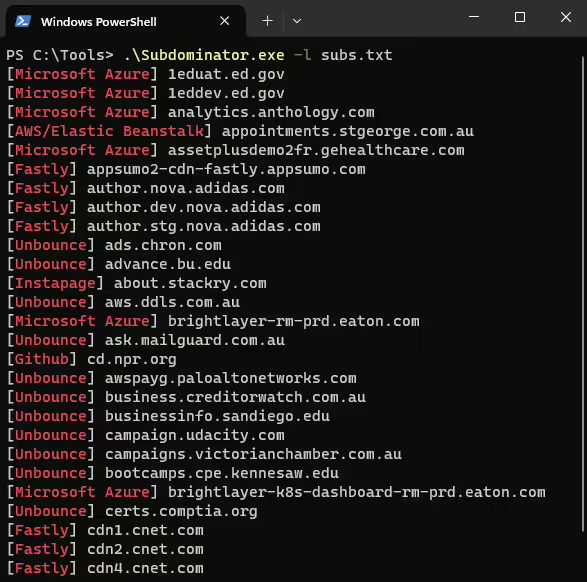
Subdominator is a dependable and fast open-source command-line interface tool to identify subdomain takeovers. It boasts superior accuracy and reliability, offering improvements compared to other tools. “Initially, Subdominator was created internally because all the current subdomain takeover tools had gaps in their functionality. No tool had a complete set of accurate service fingerprints or features. […]
The campaign sends phishing emails pretending to be from Meta, Instagram’s parent company, claiming that the recipient’s account has been restricted due to copyright infringement.
Bringing artificial intelligence into the cybersecurity field has created a vicious cycle. Cyber professionals now employ AI to enhance their tools and boost their detection and protection capabilities, but cybercriminals are also harnessing AI for their attacks. Security teams then use more AI in response to the AI-driven threats, and threat actors augment their AI […]
Israel’s National Cyber Directorate (NCD) has issued an “urgent warning” about a targeted email campaign impersonating F5 Networks that delivers a dangerous wiper malware. The lure for the attack is a critical authentication bypass vulnerability in F5’s BIG-IP, disclosed in late October. At the time, F5 said one way to resolve the vulnerability was to download and […]
The EMBA open-source security analyzer is tailored as the central firmware analysis tool for penetration testers and product security groups. It assists throughout the security evaluation procedure, extracting firmware, conducting static and dynamic analysis through emulation, and creating a web-based report. EMBA features EMBA identifies potential vulnerabilities and weak points in firmware, such as insecure […]
A new piece of JavaScript malware has been observed attempting to steal users’ online banking account credentials as part of a campaign that has targeted more than 40 financial institutions across the world. The activity cluster, which employs JavaScript web injections, is estimated to have led to at least 50,000 infected user sessions spanning North […]
Data leak exposes users of car-sharing service Blink Mobility Pierluigi Paganini December 21, 2023 More than 22,000 users of Blink Mobility should take the necessary steps to protect themselves against the risk of identity theft. The Cybernews research team has discovered that their personal data was exposed in a leak. Los Angeles-based electric car-sharing provider […]
By What is a disaster recovery team? A disaster recovery team is a group of individuals focused on planning, implementing, maintaining, auditing and testing an organization’s business continuity and disaster recovery procedures. Disaster recovery (DR) is an area of security planning focused on enabling an organization to maintain or rapidly resume mission-critical functions following a […]