Last updated 20 December, 2023 As a DJ, backing up your music and your software’s music database is paramount. The loss of these assets means not only losing the tools of your trade, but also the countless hours you’ve dedicated to building playlists, preparing songs, and more. No professional DJ would ever risk not backing […]
Four vulnerabilities, including a critical one, have been discovered in the widely used Perforce Helix Core Server, posing a significant risk to organizations in the gaming, government, military, and technology sectors.
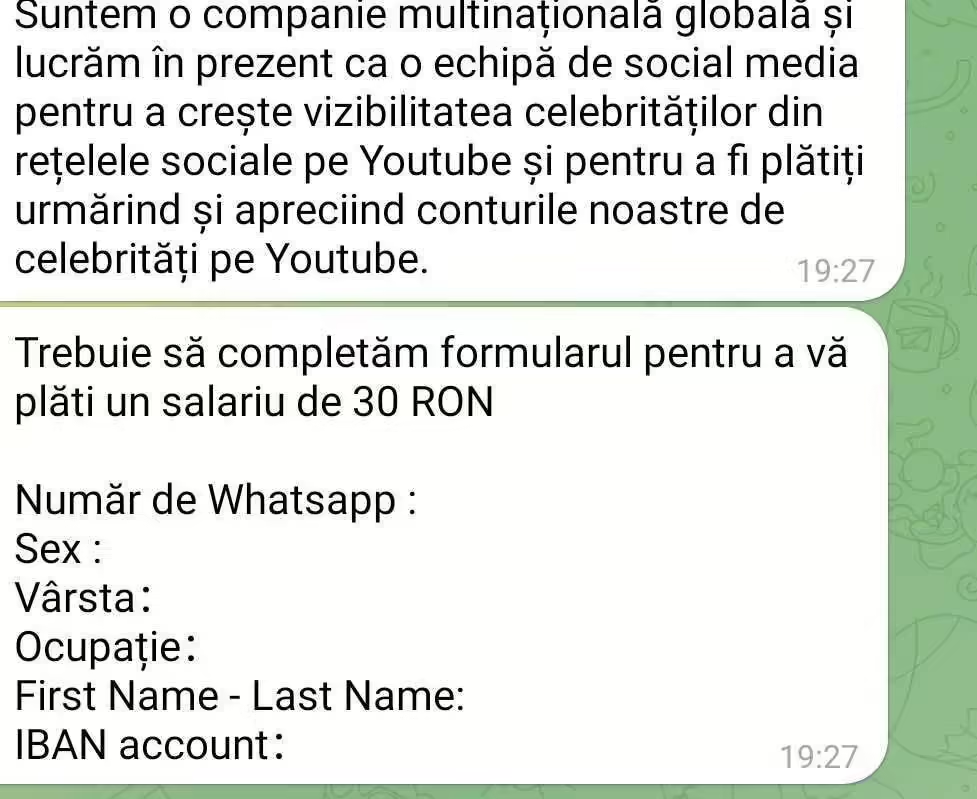
Have you ever considered a remote job that only requires you to click the like or subscribe button on YouTube videos? If you have, we’re sorry to say it’s a scam. This month, researchers at Bitdefender Labs have been taking a closer look at the latest remote job swindles polluting social media platforms – namely […]
SUMMARY Note: This joint Cybersecurity Advisory (CSA) is part of an ongoing #StopRansomware effort to publish advisories for network defenders that detail various ransomware variants and ransomware threat actors. These #StopRansomware advisories include recently and historically observed tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) to help organizations protect against ransomware. Visit stopransomware.gov […]
Dec 19, 2023NewsroomRansomware / Cybercrime The U.S. Justice Department (DoJ) has officially announced the disruption of the BlackCat ransomware operation and released a decryption tool that victims can use to regain access to files locked by the malware. Court documents show that the U.S. Federal Bureau of Investigation (FBI) enlisted the help of a confidential […]
Dec 19, 2023NewsroomRansomware / Russian Hackers Cybersecurity researchers have shed light on the inner workings of the ransomware operation led by Mikhail Pavlovich Matveev, a Russian national who was indicted by the U.S. government earlier this year for his alleged role in launching thousands of attacks across the world. Matveev, who resides in Saint Petersburg […]
The ransomware attack on Westpole is disrupting digital services for Italian public administration Pierluigi Paganini December 19, 2023 An alleged Lockbit 3.0 ransomware attack on the Italian cloud service provider Westpole disrupted multiple services of local and government organizations and municipalities. A cyber attack hit on December 8, 2023 the Italian cloud service provider Westpole, […]
The breach occurred after attackers exploited a critical vulnerability, known as Citrix Bleed, that had been actively exploited as a zero-day since August 2023. The company has asked users to reset their passwords.
A novel way to abuse a decades-old protocol used to send emails since the beginning of the Internet allows attackers to evade Domain-based Message Authentication, Reporting and Conformance (DMARC) and other email protections, putting organizations and individuals at risk for targeted phishing attacks that appear to come from legitimate sources. Using a technique called “SMTP […]