Dec 19, 2023NewsroomRansomware / Threat Intelligence The threat actors behind the Play ransomware are estimated to have impacted approximately 300 entities as of October 2023, according to a new joint cybersecurity advisory from Australia and the U.S. “Play ransomware actors employ a double-extortion model, encrypting systems after exfiltrating data and have impacted a wide range […]
Last updated 18 December, 2023 Algoriddim recently released djay Pro 5 for iOS, iPadOS, and Mac. It further refined an already smooth piece of DJ software, with an absolutely killer new feature in (possibly) the best beatgrids ever added to any software, along with world-class stems and other new features. On paper, it’s the most […]
Last updated 18 December, 2023 Tidal has spoken publicly for the first time about the removal of stems functionality in DJ software when streaming music from its service. In a statement on X, Tidal says that it believes other streaming service providers have also been asked to do this, and that it is working to […]
A new influence campaign that has gained substantial traction is pushing pro-China and anti-United States narratives on YouTube, researchers have found. According to a report released this week by the Australian Strategic Policy Institute (ASPI), the videos garnered substantial views and subscribers — a rarity in the world of social media influence operations. Named Shadow […]
ALPHV was the second-most leveraged ransomware strain in North America and Europe between January 2022 and October 2023, just before the reported takedown of the group’s website, according to ZeroFox research. The analysis found that ALPHV, aka BlackCat, accounted for around 11% of all ransomware and digital extortion (R&DE) attacks in North America over the […]
Dec 18, 2023NewsroomEmail Security / Vulnerability Technical details have emerged about two now-patched security flaws in Microsoft Windows that could be chained by threat actors to achieve remote code execution on the Outlook email service sans any user interaction. “An attacker on the internet can chain the vulnerabilities together to create a full, zero-click remote […]
Over the past few years, SaaS has developed into the backbone of corporate IT. Service businesses, such as medical practices, law firms, and financial services firms, are almost entirely SaaS based. Non-service businesses, including manufacturers and retailers, have about 70% of their software in the cloud. These applications contain a wealth of data, from minimally […]
The developers of the information stealer malware known as Rhadamanthys are actively iterating on its features, broadening its information-gathering capabilities and also incorporating a plugin system to make it more customizable. This approach not only transforms it into a threat capable of delivering “specific distributor needs,” but also makes it more potent, Check Point said […]
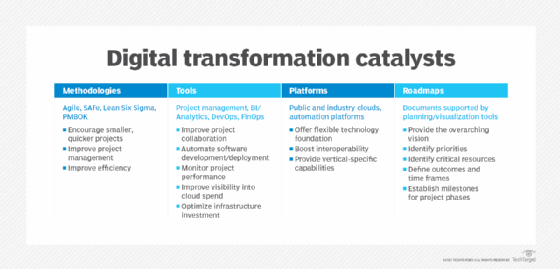
What is digital leadership? Digital leadership is the strategic use of a company’s digital assets and emerging technologies to achieve business goals. A digital leader is a person who guides this digital approach within an organization. Digital leadership is becoming more and more important with the rapidly shifting business landscape and ever-changing technology. Any organization […]
- 1
- 2