Dec 06, 2023NewsroomVulnerability / Mobile Security Chipmaker Qualcomm has released more information about three high-severity security flaws that it said came under “limited, targeted exploitation” back in October 2023. The vulnerabilities are as follows – CVE-2023-33063 (CVSS score: 7.8) – Memory corruption in DSP Services during a remote call from HLOS to DSP. CVE-2023-33106 (CVSS […]
This new update to Serato DJ has been in the mix for a bit, but this week Serato fully released Serato DJ 3.1. This new update means that owners of Official Serato Accessories (list below) can quickly and easily control Serato Stems as a pad mode, no need for a custom MIDI mapping. DJs gain […]
There’s a growing demand for third-party, on-premises data centers that enable organizations to reduce or eliminate expenses related to managing power, connectivity, space and cooling. However, selecting a data center to host an organization’s equipment is not easy, as there are numerous colocation providers that offer a multitude of services and contracts. What is colocation? […]
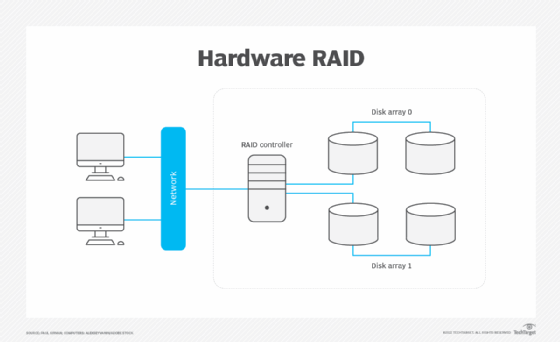
What is hardware RAID (hardware redundant array of independent disk)? Hardware RAID is a form of RAID (redundant array of independent disks) where processing is done on the motherboard or a separate RAID card. With hardware RAID, logical disks are configured and mirrored outside of the storage system. A physical RAID controller manages the array, […]
Last updated 5 December, 2023 Users of Denon DJ and Numark’s standalone equipment can now download Engine DJ 3.3, the latest version of the embedded software for their DJ gear that brings a whole host of new features. As well as profiles allowing a single login for all services and enabling cloud BPM and key […]
IBM unveiled its Condor and Heron quantum processing units Monday, which keeps the company on its own public roadmap — and by most accounts, in the lead of the quantum computing race. The Condor QPU, with 1,121 qubits, is the second fastest in the world. Heron is smaller, with 133 qubits, but can combine with […]
Dec 05, 2023NewsroomMobile Security / Spyware A new “post-exploitation tampering technique” can be abused by malicious actors to visually deceive a target into believing that their Apple iPhone is running in Lockdown Mode when it’s actually not and carry out covert attacks. The novel method, detailed by Jamf Threat Labs in a report shared with […]
Dec 05, 2023NewsroomBrandjacking / Artificial Intelligence The Russia-linked influence operation called Doppelganger has targeted Ukrainian, U.S., and German audiences through a combination of inauthentic news sites and social media accounts. These campaigns are designed to amplify content designed to undermine Ukraine as well as propagate anti-LGBTQ+ sentiment, U.S. military competence, and Germany’s economic and social […]
Sellafield reportedly infected with sleeper malware despite facility claiming “no records or evidence” to suggest attack