What happened Proofpoint researchers identified TA571 delivering the Forked variant of IcedID in two campaigns on 11 and 18 October 2023. Both campaigns included over 6,000 messages, each impacting over 1,200 customers in a variety of industries globally. Emails in the campaigns purported to be replies to existing threads. This is known as thread hijacking. […]
Nov 01, 2023NewsroomMalware / Cryptocurrency State-sponsored threat actors from the Democratic People’s Republic of Korea (DPRK) have been found targeting blockchain engineers of an unnamed crypto exchange platform via Discord with a novel macOS malware dubbed KANDYKORN. Elastic Security Labs said the activity, traced back to April 2023, exhibits overlaps with the infamous adversarial collective […]
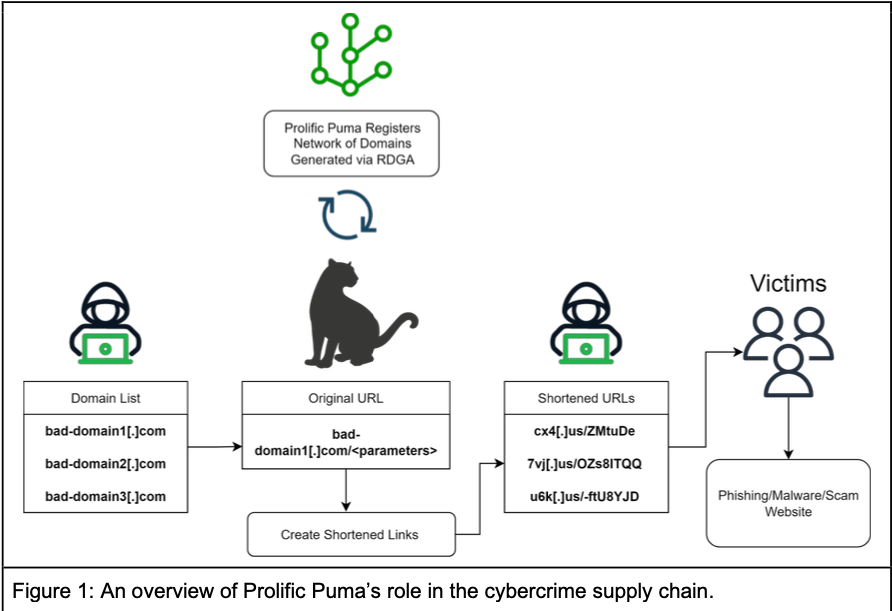
The top-level domain for the United States — .US — is home to thousands of newly-registered domains tied to a malicious link shortening service that facilitates malware and phishing scams, new research suggests. The findings come close on the heels of a report that identified .US domains as among the most prevalent in phishing attacks […]
Palo Alto Networks (NASDAQ: PANW) announced on Tuesday that it has entered into a definitive agreement to acquire Dig Security, a Tel Aviv, Israel-based provider of Data Security Posture Management (DSPM) technology. Dig Security’s DSPM solution helps organizations to discover, classify, monitor, and protect sensitive data across all cloud data stores, and will offer Palo […]
Over the Kazuar’s Nest: Cracking Down on a Freshly Hatched Backdoor Used by Pensive Ursa (Aka Turla)
Executive Summary While tracking the evolution of Pensive Ursa (aka Turla, Uroburos), Unit 42 researchers came across a new, upgraded variant of Kazuar. Not only is Kazuar another name for the enormous and dangerous cassowary bird, Kazuar is an advanced and stealthy .NET backdoor that Pensive Ursa usually uses as a second stage payload. Pensive […]
The rapid rise of hardware- and firmware-related attacks and supply chain threats has been one of the most significant changes in cybersecurity in recent years. Unlike the small incremental changes that typically define the evolution of threats (e.g. new malware variant, new ransomware operator, etc.), this new wave of attacks has introduced profound and fundamental […]
Key Findings Check Point Research (CPR) is monitoring an ongoing Iranian espionage campaign by Scarred Manticore, an actor affiliated with the Ministry of Intelligence and Security (MOIS). The attacks rely on LIONTAIL, an advanced passive malware framework installed on Windows servers. For stealth purposes, LIONTIAL implants utilize direct calls to Windows HTTP stack driver HTTP.sys […]
Nov 01, 2023NewsroomCyber Threat / Malware The Russia-linked hacking crew known as Turla has been observed using an updated version of a known second-stage backdoor referred to as Kazuar. The new findings come from Palo Alto Networks Unit 42, which is tracking the adversary under its constellation-themed moniker Pensive Ursa. “As the code of the […]