Unmasking Vacum Stealer: The Malware Plotting Cryptocurrency Plunder
A hacker forum user was found advertising Vacum Stealer, a malware that can transfer cryptocurrency from a user to the cybercriminal’s wallet. Vacum Stealer, the developer claimed would do so without requiring any additional confirmation. The malware, once accepted by the targeted individual could transfer all ERC20 tokens and ETH, the user boasted.
The seller on the dark web marketplace was also the developer of Vacum Stealer which they worked on for five months during an NFT campaign, they added to the post.
Working of Vacum Stealer
Cybercriminals can buy this ETH stealer for €250 (in Monero) and pose a risk to unsuspecting users. The Vacum Stealer was endorsed by a dark web user named Mercidoctor who joined the forum on 06-10-2022.
It is worth noting that the seller claimed that the ETH stealer which could transfer ERC20 tokens to their wallet could be deployed on a website. Following this, it would show a fraudulent crypto wallet link to the user.
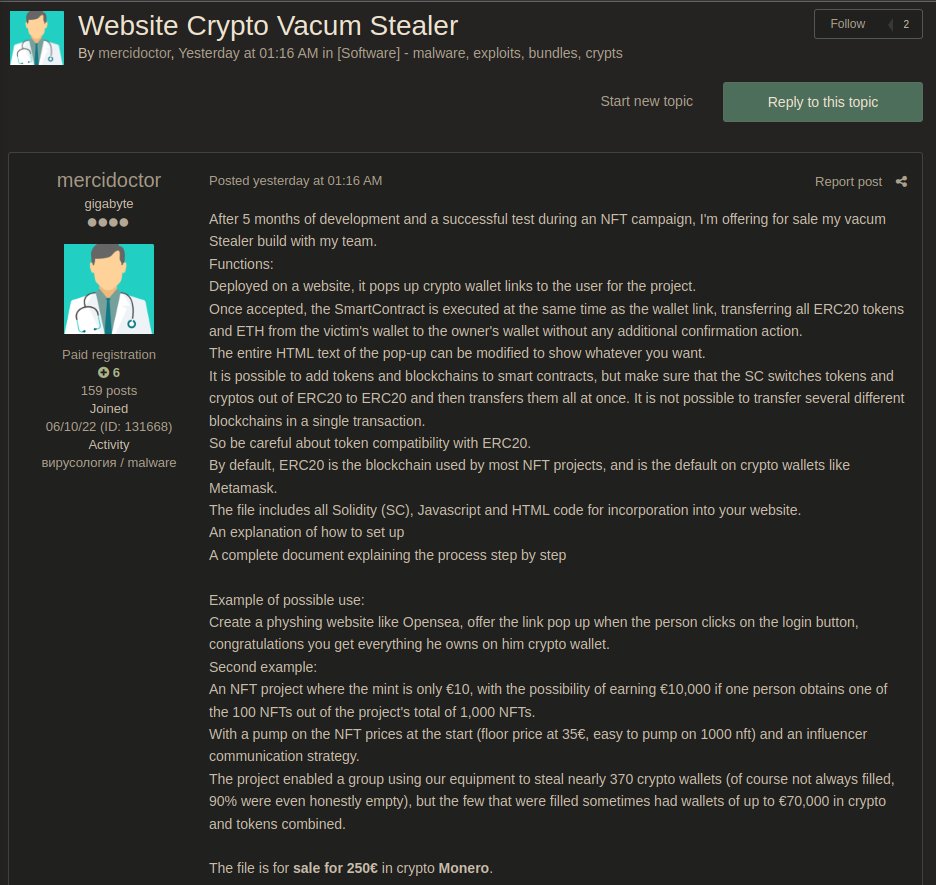
In case unsuspecting users access the link, a Smart contract gets executed likely with fraudulent agreements and other details. At the same time, the wallet link also is executed which, according to the seller, leads to the transfer of all ERC20 tokens and ETH from their wallets to the scammer’s account.
It is advised that users stir clear of pop-ups that may have infected links not showing their original content and intent. Also, websites that offer cryptocurrency wallet-related content need not always have genuine links and content.
Criminal coders make every effort to innovate, adaptable malware that works on websites and evades detection. Hence, it becomes difficult to detect and so users must not trust random online sources for financial or personal information-related works.
Any sudden transactions must be immediately brought to the attention of the firm to prevent further credential and financial losses.
The ERC20 tokens stealer advertisement further added, “It is not possible to transfer several different blockchains in a single transaction.” This further establishes the importance of reporting unauthorized transactions to prevent further losses.
Scammers will be aiming to make more transactions which gives the targeted individual the time to stop it after receiving a notification of the first transfer.
To further understand how to prevent threats, it would help to learn the process used to make fraudulent transactions using the ERC20 tokens stealer. The process outlined steps for scammers who might buy the Vacum Stealer to commit token fraud.
The first process that was explained was as follows:
- Create a phishing website like Opensea.
- Offer the link pop-up
- When the person clicks on the login button, the transactions will take place
Phishing websites are a lucrative source of gaining the trust of users. Developers make compelling content that may have icons, links, pages, and offers to drive the interest of users. If a user is desperate to gain a profit from schemes, such phishing websites may dupe them instead.
The second example was creating a project offering €10 with a promise to offer more and using an influencer communication strategy.
It is urged to steer clear of influencer communications and content that come with a promise of higher rewards on a small investment. A small investment might be worth losing for some however, crypto-stealing malware may go for the bigger loot without them realizing it.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.