Exploited SSH Servers Offered in the Dark web as Proxy Pools
Aqua Nautilus researchers have shed brighter light on a long-standing threat to SSH in the context of the cloud. More specifically, the threat actor harnessed our SSH server to be a slave proxy and pass traffic through it. In this blog, we will explain this threat, demonstrate how attackers exploit SSH, what actions they take upon gaining initial access, and the implications of these attacks on organizations and businesses.
Explaining SSH Tunneling in an Attack Context
In this section, we will clarify what SSH tunneling is and how attackers employ it.
What is SSH Tunneling?
SSH tunneling is a technique used to establish secure and encrypted network connections between two servers, allowing data to traverse safely over an untrusted network. Its primary purpose is to create a secure communication channel between a local and a remote host, which can then be utilized to tunnel various network protocols and services.
SSH Tunneling Used in Proxy Pools
A proxy pool refers to a collection of proxy servers available for individuals or applications to route their internet traffic through. Proxies serve as intermediaries between a user’s device and the internet, enabling users to conceal their IP addresses, access geo-restricted content, enhance privacy, and more.
In the context of the SSH campaigns observed in our honeypots’ environments, there is substantial evidence indicating that the targeted SSH servers are offered in the dark web as part of proxy pool packages.
SSH Tunneling Used for Spam Dissemination
Spamming involves the practice of sending unsolicited and often irrelevant or inappropriate messages or content to a large number of recipients. We frequently encounter spam dissemination through the exploitation of web applications, account takeovers, malware, etc.
Spamming is rarely discussed in the context of cloud-native environments. However, one dissemination vector worth mentioning and explaining is that threat actors also employ SSH tunneling.
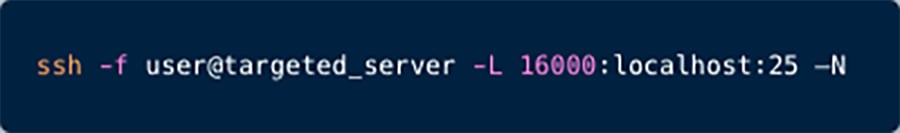
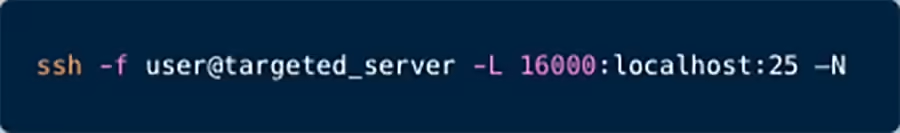
Figure 1: SSH Tunneling Command Example
Figure 2: SSH Tunneling Attack That Disseminates Email via SMTP
As illustrated in Figure 2 above, the threat actor can connect via SSH to a target server. Subsequently, the threat actor sets up an SSH tunnel to forward port 25 back to their system, to which they locally connect to any given port (e.g., port 16000 in our example) for disseminating malicious content or spam.
How Do Threat Actors Gain Initial Access?
In our context, we have outlined two plausible scenarios. We have observed evidence of brute force attacks on our SSH honeypots, and we highlight this as the primary initial access vector. Additionally, we have seen campaigns that conduct post-exploitation lateral movement to SSH connections.
Use Cases from Our Honeypots
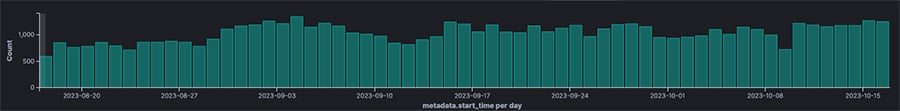
As depicted in Figure 3 below, there are approximately 1,000 attacks per day on a single honeypot on average. This means that we receive a connection request roughly every 40 minutes. Each connection request often involves hundreds of sessions, frequently containing various malicious activities.”
Figure 3: Average daily attack trend over a period of 2 months on a single honeypot, limited to SSH tunneling attack
We have documented numerous types of attacks on our honeypots. Below, we will review some of them:
SSH Tunneling
The majority of these attacks utilize the SSH protocol, including various SSH versions such as OpenSSH, Paramiko, libssh, NmapSSH, WinSCP, etc. Due to the encryption of the data, we were unable to perform further analysis on the content of these attacks. Consequently, we are left to assume that these attacks exhibit significant variability, and their exact nature remains unknown at this time. We have observed extensive communication with various domains, including Gmail, iCloud, Microsoft, gmx.com, Discord, and more. This could potentially indicate further email dissemination through online web services.
Malicious Activities
We have detected numerous requests to various email services, such as Gmail and gmx, resulting in denials due to various failures. Given the frequency of these attempts, we suspect they may be brute force attacks. Additionally, we have identified instances of cryptomining activity and script kiddies running various scripts.
Intelligence Collection
We have also observed domain lookup requests attempting to retrieve ‘Whois’ data and geolocation requests seeking information about IP addresses. We are familiar with such behavior from various cloud attacks. These techniques allow attackers to obtain the IP address of a random server they successfully infiltrate.
Furthermore, we have noticed API requests directed at various services, including the Steam API. Steam is a gaming website, and it appears that these requests were aimed at collecting intelligence on various users.
Figure 4: Steam Gaming Website
Spamming and Fraud
We have detected significant activity involving ESMTP and SMTP protocols used for email dissemination. These emails encompassed various content types, including adult content, job offers, financial gains, prizes, lotteries, loan offers, fortune-telling, and more. These messages often attempted to entice targets into divulging sensitive information such as credentials or downloading malware.
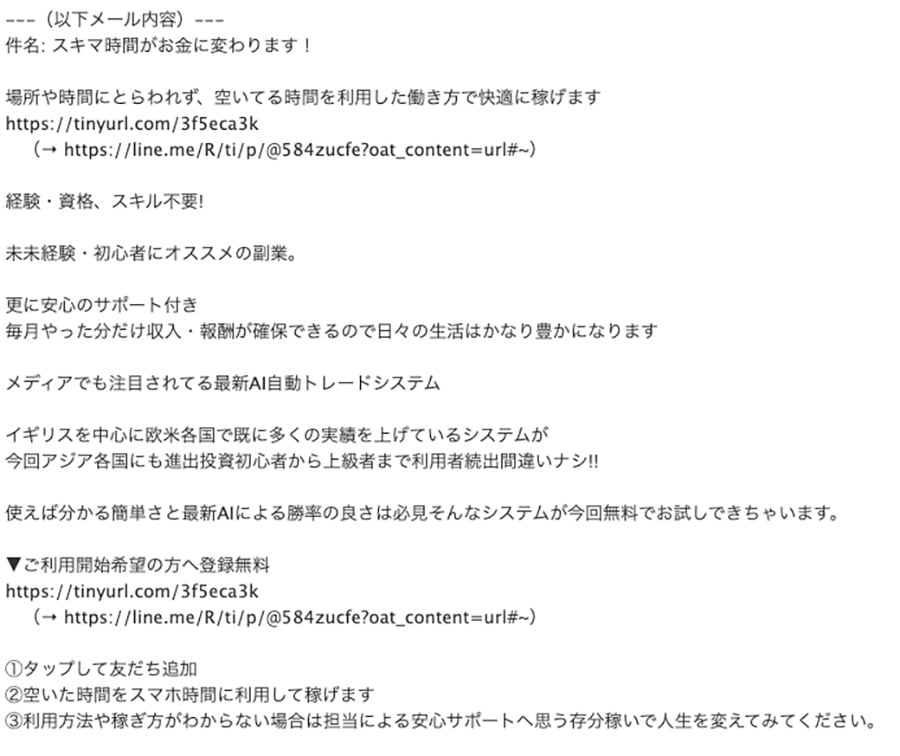
Figure 5 and 6: Fraudulent Emails in Japanese (Original) and English Translation
As shown in Figure 6 above, one email’s subject reads, “Turn your free time into money!” The attackers encourage victims to add a user to their “Line” application, leading to further fraudulent activities conducted by a live fraudster who coerces the victim into providing money.
We have also encountered evidence of affiliate marketing fraud attempts and content scraping.
Why Should We Be Concerned About SSH Tunneling?
First, attackers can gain complete control over a server through compromised SSH access. Second, even if you are dealing solely with SSH tunneling, it can have a significant impact on your organization and business. Your IP address’s reputation can be severely tarnished, potentially leading to IP address bans that disrupt outbound email, data, or other traffic. Your business reputation may also suffer due to associations with fraudulent or malicious activities. Therefore, even without experiencing a data breach, this type of attack can still negatively affect your business.
Detection and Mitigation with Aqua’s CNAPP
Utilizing Aqua’s cloud native application protection platform (CNAPP) you can both detect misconfiguration in your SSH servers and malicious behavior stemming from an attack of a threat actor.
Below are actionable recommendations that can be taken to ensure your impacted environments safety:
- Prevent unnecessary SSH access.
- Use network monitoring tools to block or limit inbound/outbound traffic.
- Employ strong, unique passwords or key-based authentication for SSH access.
- Implement multi-factor authentication (MFA) to enhance SSH security.
- Monitor SSH logs for unusual activities or multiple failed login attempts.
- Regularly update and patch SSH software to mitigate known vulnerabilities.
- Consider using SSH certificate-based authentication for increased security.
- You can easily block tunneling of ports by changing: “AllowTCPForwarding no”
Summary
The analysis of attacks on our honeypots reveals a diverse range of threats, with several common attack vectors identified. These include SSH tunneling, malicious activities such as brute force attacks and cryptomining, intelligence collection techniques, and spamming/fraud via email dissemination. To mitigate these threats, organizations should implement strong SSH security practices, employ intrusion detection systems, educate users about email security, and monitor network traffic for unusual activities. Additionally, maintaining IP address reputation and prompt response to abuse reports are essential for protecting business interests and reputation.