Escalation of Fake E-Shop Campaign Threatens Banking Security in Multiple Regions
A recent analysis by Cyble has revealed a concerning escalation in the fake e-shop campaign, signaling a looming threat to banking security across various regions.
Initially focused on Malaysian banks, this e-shop phishing campaign has now extended its reach to financial institutions in Vietnam and Myanmar.
What sets this phishing campaign apart from others on the web is its integration of Android malware equipped with screen-sharing capabilities.
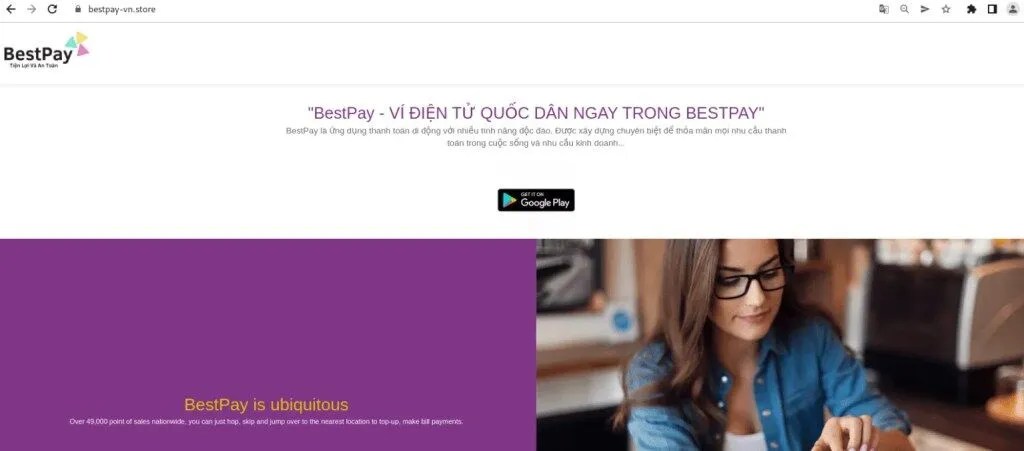
The enhanced variant of the fake e-shop campaign represents an expert level of sophistication, evading detection and using the best of social engineering tactics. By leveraging these tools, threat actors behind the campaign have started targeting financial institutions in pursuit of illicit gains.
The Unprecedented Rise of Fake E-Shop Campaign
The threat actor behind the fake e-shop campaign leverages tools such as the open-source string obfuscator “Paranoid” and the Janus WebRTC module, showcasing a deep understanding of technological intricacies to evade detection and amplify their impact.
According to a Cycle Research and Intelligence Lab (CRIL) report, the origins of this phishing campaign can be traced back to 2021, when it initially targeted Malaysian banks through deceptive tactics.
Victims were lured into the scam through fake cleaning service pages on social media platforms, eventually leading them to phishing sites where they were prompted to download malicious APK files.
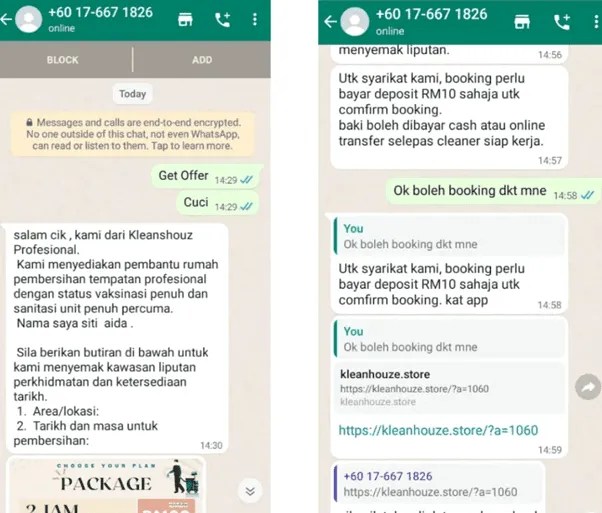
Over time, the campaign expanded its scope to include a broader array of Malaysian banks, such as Hong Leong Bank, CIMB Bank, and Maybank.
Widening the Net: 10+ Phishing Websites Running in the Wild
In September 2022, the campaign took a new turn by extending its operations to Vietnam, followed by Myanmar in November of the same year. The modus operandi remained consistent: lure victims through phishing sites masquerading as legitimate payment applications and lure them into downloading malicious files.
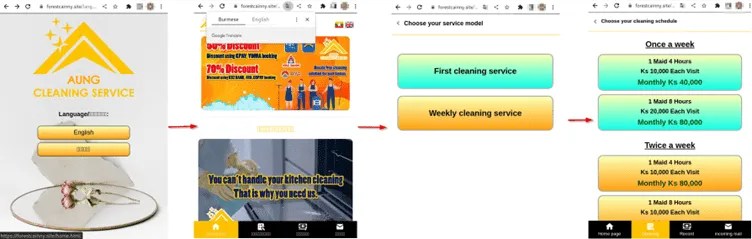
The targets in these regions included prominent banks like Kanbawza Bank and Yoma Bank, amplifying the campaign’s reach and impact. According to CRIL, the recent updates to the fake e-shop campaign have revealed over ten identified phishing sites posing as online shopping platforms. These websites include:
- hxxps://shopcenter-global[.]com
- hxxps://worldshopping-global[.]com
- hxxps://onlineshop-global[.]com
- hxxps://www[.]weshop-global[.]com
- hxxps://shopcenter-global[.]com
- hxxps://shopbox-global[.]com
- hxxps://myshopping-global[.]com
- hxxps://www[.]mystore-global[.]com
- hxxps://ecart-global[.]com
- hxxps://goshop-global[.]com
- hxxps://everydaystore-global[.]com
- hxxps://easyshop-global[.]com/
These sites feature downloadable Android applications, which, upon installation, unleash a barrage of sophisticated malware. The latest version of the malicious application incorporates advanced features such as screen sharing via the Janus WebRTC plugin and exploitation of accessibility services, further complicating detection and mitigation efforts.
Mitigation Practices Against the Fake E-Shop Campaigns
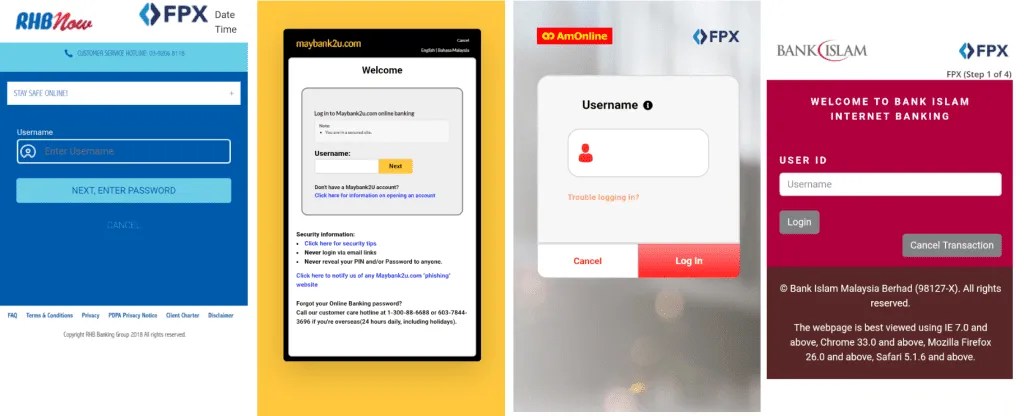
Given the nature of cyber threats like e-shop phishing and the proliferation of e-commerce phishing sites, individuals and organizations need to differentiate between phishing sites and authentic ones using certain parameters. These can include, checking URLs for errors, verify SSL encryption, and authenticating professional design and contact info.
As a part of the mitigation strategies, CRIL suggest that users can exercise caution when downloading apps, implementing reputable antivirus software, and scrutinizing permissions granted to applications. Additionally, staying vigilant against suspicious links and regularly updating devices and software can help fortify defenses against potential attacks.
The escalation of the fake e-shop campaign highlights the dynamic nature of threat actors and the cunning methods they employ. By targeting financial institutions across multiple regions and employing advanced tactics, threat actors pose a big risk to both personal and organizational security.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.

