PolyCrypt Runtime Crypter Being Sold On Cybercrime Forums | BlackFog
This article provides a comprehensive look at crypters, software that disguises malware to evade antivirus detection. The discussion covers the basic operations of crypters, their increasing use in cybercrime, as well as the specifics of how PolyCrypt functions.
Any tool or technique that promotes secrecy is music to the ears of dubious malicious attackers, who rely on secrecy to exploit vulnerabilities. Crypters (or cryptors), the software that “masks” malware, are an attacker’s delight because of their stealthiness. The software conceals malicious code to make it fully undetectable (FUD) by security products.
Static Crypters
Stubs, which are parts of the code used to encrypt and decrypt malicious code, determine the complexity of crypters. Static crypters encrypt files using unique codes. The unique code (or stub) is responsible for encrypting and decrypting the code after execution. It also facilitates modifications for attackers, particularly after security detection.
Polymorphic Crypters
Meanwhile, polymorphic crypters take code manipulation to a higher standard. They use advanced algorithms to weaponize duplicity. The complex code uses random variables, keys, decoders, and more to produce unique code files. As a result, input source files will never replicate identical output files. For this reason, signature-based security products struggle to detect the output of polymorphic crypters because they constantly change their signature while retaining functionality.
Scantime Crypters
Scantime and runtime crypters represent two primary detection modes in the realm of crypters.
Scantime crypters are designed to render malware undetectable while it’s in a dormant state, that is, when it’s stored on a disk but not yet executed. As explained by cybersecurity firm Zerofox, “A scantime crypter can effectively disguise malware from antivirus software during a file scan.” However, since it’s necessary to decrypt the file before running it, antivirus software might be able to detect the malware while it’s in operation.
Runtime Crypters
On the other hand, runtime crypters add an extra layer of stealth. Like scantime crypters, they aim to make malware undetectable prior to execution. However, unlike scantime crypters, runtime crypters can decrypt and run the malware while it’s active, thereby bypassing detection during the execution process. Instead of decrypting the entire malware file before it runs, runtime crypters decrypt only the parts of the malware file needed for a specific task and load them into memory as a separate process before execution. After the malware is launched, the stub code re-encrypts it, making the malware fully undetectable and thus more stealthy than scantime crypters.
Popularity
Crypters have been popular among threat actors for years. For instance, the cybersecurity company Trend Micro, alongside the National Crime Agency (NCA), seized malware websites (reFUD.me and Cryptex Reborn) that provided crypter services in 2015. reFUD.me allowed developers to scan and modify illegal files to make them undetectable, while Cryptex Reborn provided malware delivery using encryption.
Likewise, in 2020, the European authorities arrested suspects for allegedly running crypter services that helped malicious actors evade anti-malware systems. “Approximately 300 malware files modified by using the illegal services CyberSeal and DataProtector could be identified and used to launch cyberattacks on computer systems around the world, including Romania,” the Romanian police said about the suspects’ activities.
Similarly, Fortinet attributed the spike in injection activities to crypter services in May 2023. For example, malware families (e.g., AsyncRAT, njRAT, and NanoCoreRAT) used SYK Crypter to deliver Remcos, a Remote Administration Tool (RAT) used for controlling and monitoring devices operating on Windows.
PolyCrypt: The Malicious Crypting Harbour
The underground market (usually cybercrime forums) is the platform for selling crypters. PolyCrypt, a web-based polymorphic crypter website, has made its way to the underground market, where cybercriminals use it to accomplish their malicious malware delivery goals.
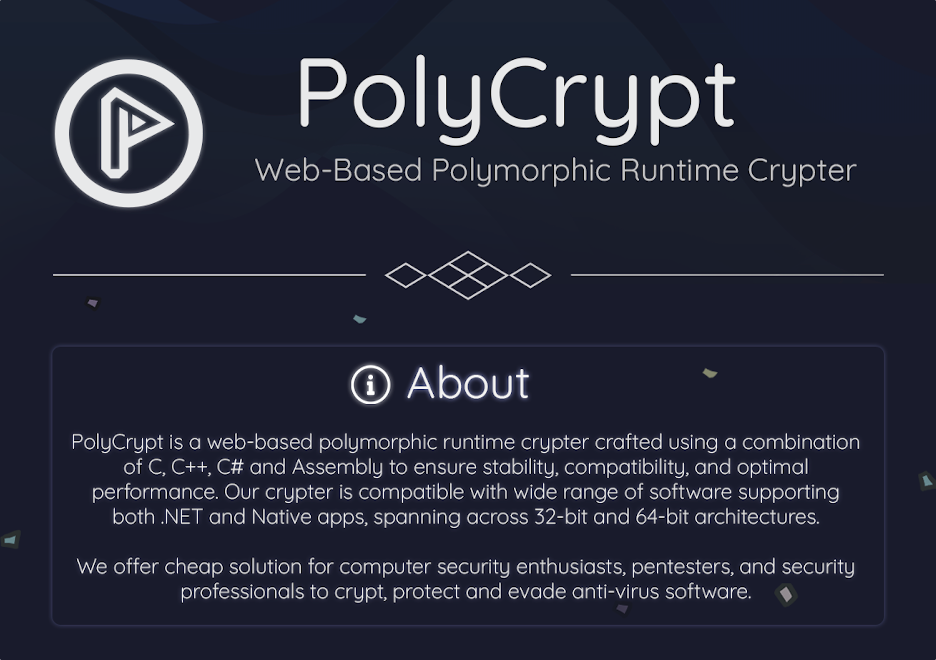
Although PolyCrypt is primarily marketed towards “security enthusiasts, pentesters, and security professionals,” it is apparent that individuals are also using it for malicious purposes, specifically cybercriminals. This can be observed through its availability for sale on various cybercrime-oriented forums. Conversations within these advertisement threads provide compelling evidence of this.
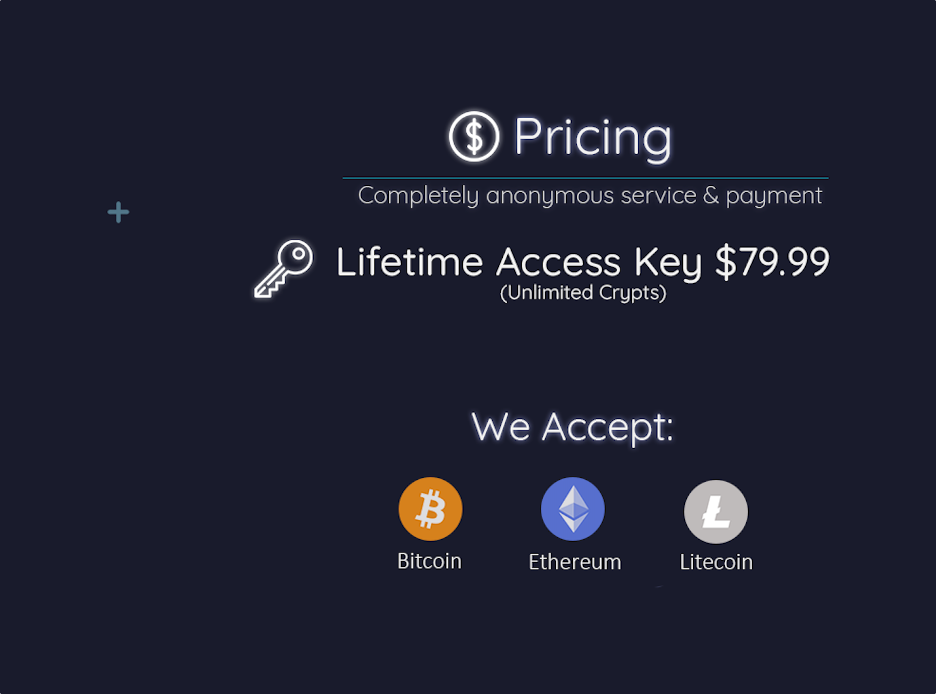
PolyCrypt Pricing
Besides ease of use, the software tool is inexpensive. The author offers a “Lifetime Access Key” (unlimited crypts) for $79.99. The pricing aligns with the low barrier-to-entry cost allure that malware operators provide to cybercriminals. It also falls within the average price range for crypters in underground forums. Similar to a lot of other malware projects, PolyCrypt accepts cryptocurrency (Bitcoin, Ethereum, and Litecoin).
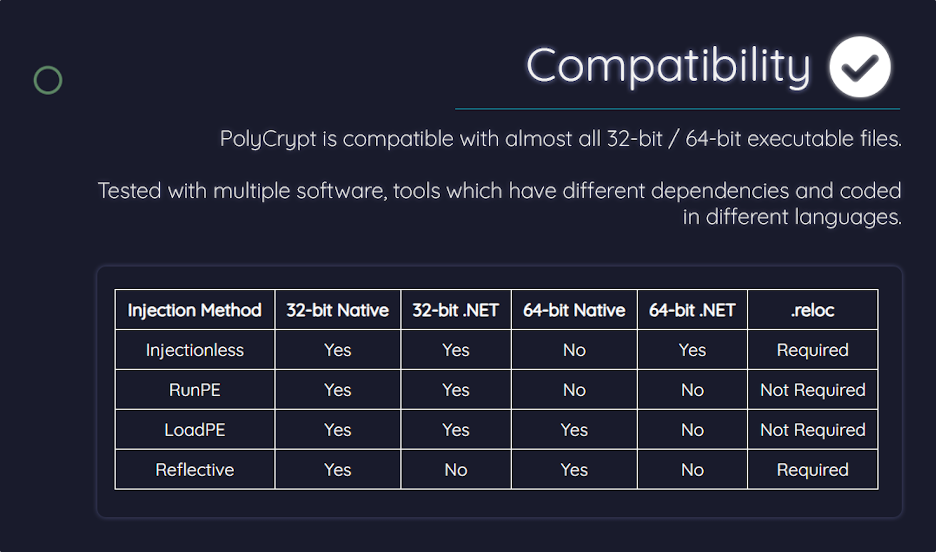
PolyCrypt Compatibility
The platform uses the C family of programming languages (C, C++, and C#). Additionally, it supports native apps and software programs that run on .NET, ensuring it can spread malware on Windows, Linux, macOS, iOS, and Android. PolyCrypt uses different portable executable (PE) packers (e.g., RunPE, LoadPE, Reflective, and injectionless) to inject malware undetected in almost every 32-bit and 64-bit executable file.
PolyCrypt Features
Like many crypters, PolyCrypt provides three main features: obfuscation, encryption, and heuristic bypass. Crypters employ both obfuscation and encryption techniques to alter the appearance and structure of original binary .exe files, making them harder to analyse and detect. One method they might use is the “end of file” (EOF) technique, where data is stored at the end of a file to enhance stealth. These manipulation techniques allow crypters to conceal identifiable strings, which could otherwise assist security products in determining malicious behaviour. Additionally, to further increase stealth, the icon of the encrypted output might be altered.

PolyCrypt is a crypter designed to encrypt malware, helping it evade detection. It has the ability to manipulate subsystems, and clone or spoof digital certificates to bypass security measures. Given its advanced capabilities, PolyCrypt can be used to remotely deploy trojans for stealing sensitive information. In their phishing campaigns, malicious actors might use PolyCrypt to encrypt malware included in email attachments.
Polycrypt Prevention
Cyberthreats are growing more advanced, from sophisticated malware to insider attacks. BlackFog provides complete protection against Polycrypt and other crypters. Using behavioral analysis and anti data exfiltration it provides insider threat and ransomware protection across endpoints before any damage can occur.
BlackFog reinforces compliance and secures sensitive data wherever it resides and provides critical cyber resilience.

