MEDUSA Ransomware Group Targets Two New Victims, Sets Ransom Deadline!
The notorious MEDUSA ransomware group has struck again, targeting two prominent companies and demanding hefty ransoms for the release of encrypted data.
The victims of MEDUSA Cyber Attacks, identified as Karam Chand Thapar & Bros. (Coal Sales) Ltd based in India, and Windak Group, are the latest additions to the dark web portal of the MEDUSA ransomware group.
Both attacks were listed on the threat actor’s dark web portal, where it shares the latest victims on the dark web.
In this space, the MEDUSA ransomware group has shared many victims in the past weeks. The addition of Karam Chand Thapar & Bros. and Windak as victims on the list shows the growing threat of the MEDUSA ransomware group.
MEDUSA Cyber Attacks Spree: Two New Victims Added!
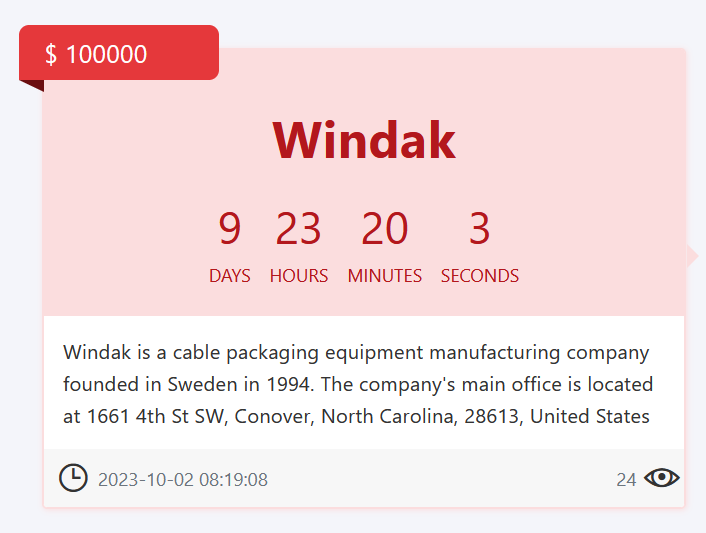
For Windak Group, a Sweden-based cable packaging equipment manufacturer founded in 1994, the threat actors have set a ransom amount of $100,000.
The deadline for payment stands at 9 days, 23 hours, 20 minutes, and 3 seconds from the time of the cyber attack.
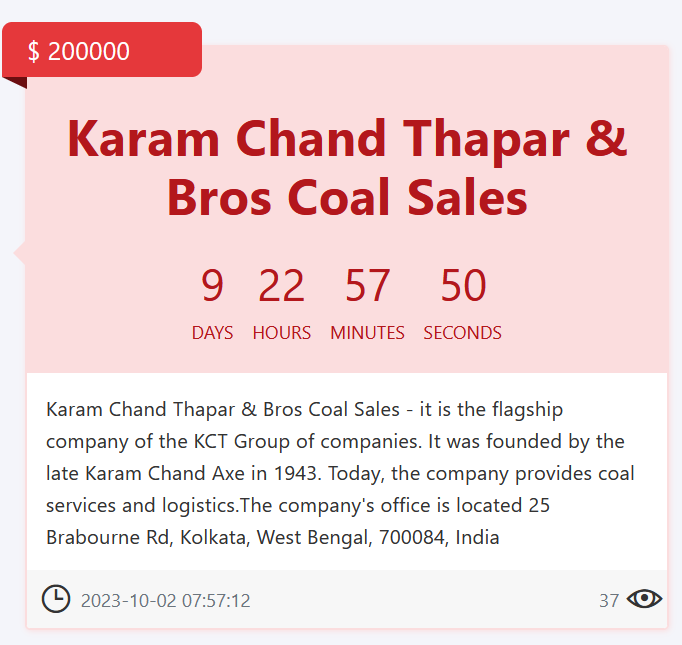
Meanwhile, Karam Chand Thapar & Bros., the flagship company of the KCT Group in India, has been targeted with a ransom of $200,000.
The threat actors have given a deadline of 9 days, 22 hours, 57 minutes, and 50 seconds for the payment. Established in 1943 by the late Karam Chand Axe, the company specializes in coal services and logistics.
Efforts to verify these claims have been initiated by The Cyber Express, which has reached out to both companies. At the time of writing, no official response has been received, leaving the MEDUSA cyber attack claims unverified.
Additionally, the victim websites appear to be operational, showing no visible signs of the cyber attack on their front end, adding a layer of uncertainty to the situation.
Previously, TCE reported a similar pattern of MEDUSA cyber-attacks where the threat actor used the same method to announce their victims.
In the previous altercation, the MEDUSA ransomware group added two major entities to their dark web portal, Landstar Power Ontario Inc. and Acoustic Center.
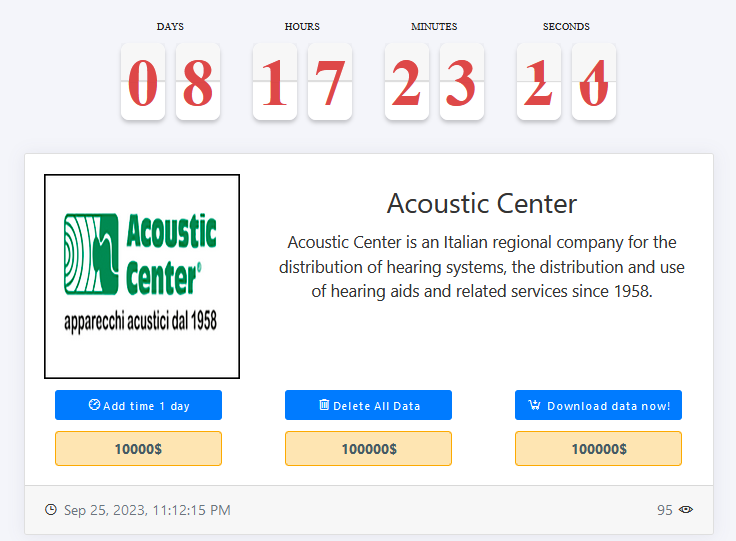

Like this particular attack, the previous ones were the same as well where the threat actor uses its dark web platform to share the announcement about the alleged cyber attacks.
At this point, this method has become a go-to for the threat actor that keeps repeating the same tactics for its cyber attack claims.
MEDUSA Cyber Attacks, Emergence, and Modus Operandi
The MEDUSA ransomware group, known for its MedusaLocker Ransomware, emerged in September 2019 and primarily targets Windows machines through SPAM campaigns.
This ransomware exhibits a unique behavior by booting up in safe mode before encryption, employing BAT files and PowerShell, depending on the variant. Notably, the latest variant alters the Bootmgr extension, resulting in an error during boot-up.
Operating under a ransomware-as-a-service (RaaS) business model, the Medusa ransomware predominantly focuses on healthcare, education, and enterprises handling substantial volumes of personal information.
The group utilizes a double extortion tactic, pilfering victim data before encryption and threatening its sale or public release if the ransom is not paid.
The ransomware predominantly exploits vulnerable Remote Desktop Protocols (RDP) and employs deceptive phishing campaigns for initial access.
Once inside a system, Medusa ransomware group employs PowerShell for command execution, systematically erasing shadow copy backups to hinder data restoration.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.