Medusa Ransomware Group Claims Cyberattack on Canadian Psychological Association
The Canadian Psychological Association (CPA), the primary representative body for psychologists across Canada, has allegedly fallen victim to a cyberattack by the notorious Medusa ransomware group.
This incident highlights the increasing threats posed by cybercriminals targeting organizations with sensitive information. The CPA, established in 1939 and incorporated under the Canada Corporations Act in May 1950, now grapples with the aftermath of this breach.
The Canadian Psychological Association Cyberattack
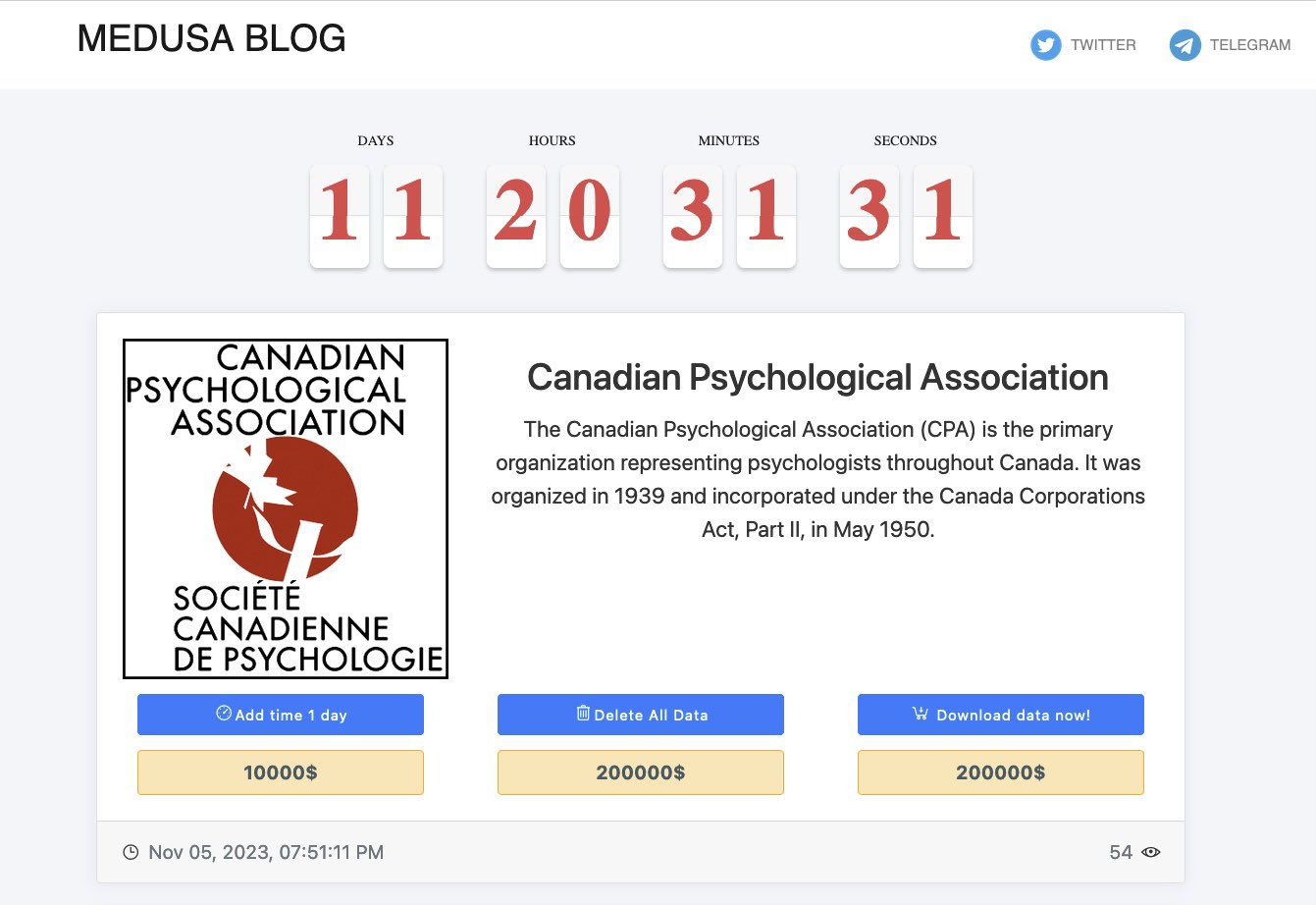
Medusa, a notorious cyber threat actor, has claimed responsibility for the attack on the CPA. The group shared details of the Canadian Psychological Association data breach on their dark web channel, “MEDUSA BLOG”, including a countdown timer adding pressure to the situation.
They have imposed ultimatums, demanding $10,000 to delay the publication of compromised data by another day, and a staggering $200,000 for the complete deletion of the data, which can then be downloaded again.
As of now, the CPA has not issued an official response or statement regarding the Canadian Psychological Association data breach. The Cyber Express has reached out to the organization to gather insights into the incident, but no information has been provided at the time of writing.
Medusa Ransomware Group Recent Attacks
This cyberattack on the CPA is not an isolated incident. Recently, the Minneapolis Public School (MPS) District experienced a large scale ransomware attack. In this case, highly sensitive information about students and teachers, including allegations of abuse and psychological reports, was exposed on the internet.
MPS initially refused to pay a $1 million ransom and successfully restored their encrypted systems through backups. However, the Medusa hacking group had not only encrypted the data but also exfiltrated their own copy, subsequently publishing it on the web and promoting it through links on a Telegram channel.
Understanding the MedusaLocker Ransomware
MedusaLocker Ransomware, first observed in September 2019, primarily targets Windows machines through SPAM. This malware exhibits unique behavior, including booting up in safe mode before execution and file encryption. It utilizes BAT files and PowerShell depending on the variant. The infected machine may encounter errors during boot-up due to alterations made by the latest variant.
Following initial access, MedusaLocker spreads through a network via a batch file executing a PowerShell script. It disables security and forensic software, restarts the machine in safe mode to evade detection, and then employs AES-256 encryption to lock files. Additionally, it eliminates local backups, disables start-up recovery, and leaves a ransom note in every folder containing compromised data.
This is an ongoing story and The Cyber Express is keeping a close look at the Canadian Psychological Association data breach. We’ll update this post once we have more information on the alleged attack.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.