Cisco security appliance 0-day is under attack by ransomware crooks

Cisco on Thursday confirmed the existence of a currently unpatched zero-day vulnerability that hackers are exploiting to gain unauthorized access to two widely used security appliances it sells.
The vulnerability resides in Cisco’s Adaptive Security Appliance Software and its Firepower Threat Defense, which are typically abbreviated as ASA and FTD. Cisco and researchers have known since last week that a ransomware crime syndicate called Akira was gaining access to devices through password spraying and brute-forcing. Password spraying, also known as credential stuffing, involves trying a handful of commonly used passwords for a large number of usernames in an attempt to prevent detection and subsequent lockouts. In brute-force attacks, hackers use a much larger corpus of password guesses against a more limited number of usernames.
Ongoing attacks since (at least) March
“An attacker could exploit this vulnerability by specifying a default connection profile/tunnel group while conducting a brute force attack or while establishing a clientless SSL VPN session using valid credentials,” Cisco officials wrote in an advisory. “A successful exploit could allow the attacker to achieve one or both of the following:
- Identify valid credentials that could then be used to establish an unauthorized remote access VPN session.
- Establish a clientless SSL VPN session (only when running Cisco ASA Software Release 9.16 or earlier).
The ASA is an all-in-one security device that provides firewall, antivirus, intrusion prevention, and virtual private network protections. The FTD is Cisco’s next-generation device that combines the ASA capabilities with a finer-grained management console and other more advanced features. The vulnerability, tracked as CVE-2023-20269, stems from the devices’ improper separation of authentication, authorization, and accounting in remote access among their VPN, HTTPS management, and site-to-site VPN features. It has a severity rating of 5.0 out of a possible 10.
Researchers from security firm Rapid7 reported last week that they had observed credential-stuffing and brute-force attacks against ASA devices since at least last March. The attacks were coming from Akira and targeted devices that didn’t have multi-factor authentication enforced for some or all of its users, the researchers said.
“Rapid7 identified at least 11 customers who experienced Cisco ASA-related intrusions between March 30 and August 24, 2023,” the August 29 post, headlined “Under Siege: Rapid7-Observed Exploitation of Cisco ASA SSL VPNs,” stated. “Our team traced the malicious activity back to an ASA appliance servicing SSL VPNs for remote users. ASA appliance patches varied across compromised appliances—Rapid7 did not identify any particular version that was unusually susceptible to exploitation.”
The attacks, as illustrated in an image included in the Rapid7 post, often directed multiple login attempts at a target in rapid succession. While both login attempts captured in the pictured activity log were unsuccessful, attackers in some cases “successfully authenticated on the first try, which may indicate that the victim accounts were using weak or default credentials.”
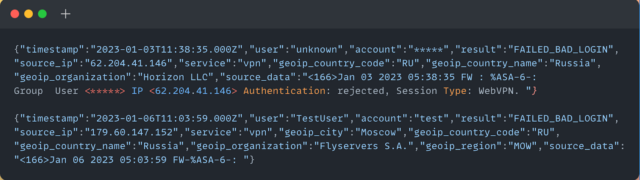
The researchers continued:
In most of the incidents we investigated, threat actors attempted to log into ASA appliances with a common set of usernames, including:
- admin
- adminadmin
- backupadmin
- kali
- cisco
- guest
- accounting
- developer
- ftp user
- training
- test
- printer
- echo
- security
- inspector
- test test
- snmp
The above is a fairly standard list of accounts that may point at use of a brute forcing tool. In some cases, the usernames in login attempts belonged to actual domain users. While we have no specific evidence of leaked victim credentials, we are aware that it’s possible to attempt to brute force a Cisco ASA service with the path +CSCOE+/logon.htm. VPN group names are also visible in the source code of the VPN endpoint login page and can be easily extracted, which can aid brute forcing attacks.
Upon successful authentication to internal assets, threat actors deployed set.bat. Execution of set.bat resulted in the installation and execution of the remote desktop application AnyDesk, with a set password of greenday#@!. In some cases, nd.exe was executed on systems to dump NTDS.DIT, as well as the SAM and SYSTEM hives, which may have given the adversary access to additional domain user credentials. The threat actors performed further lateral movement and binary executions across other systems within target environments to increase the scope of compromise. As mentioned previously, several of the intrusions culminated in the deployment and execution of Akira or LockBit-related ransomware binaries.
The researchers went on to report a guide on breaking into corporate accounts advertised for sale in crime forums. In the manual, the seller claimed to have compromised 4,865 Cisco SSL VPN services and 9,870 Fortinet VPN services using the username/password combination test:test. The post speculated that the circulation of the manual contributed to an uptick in credential attacks against Cisco ASAs.
The Rapid7 report was published five days after a principal engineer on Cisco’s product security incident response team warned customers that the company was aware of credential attacks on ASAs. He advised customers to use strong passwords and enforce MFA for all users.
It’s currently unknown when a patch will be released for CVE-2023-20269. Cisco’s Thursday advisory said that, in addition to the above guidance regarding passwords and MFA, customers can take the following steps to protect themselves from the ongoing attacks:
- Configure a dynamic access policy to terminate VPN tunnel establishment when the DefaultADMINGroup or DefaultL2LGroup connection profile/tunnel group is used
- Deny Remote Access VPN Using the Default Group Policy control
- Restrict Users in the LOCAL User Database
- Lock Users to a Specific Connection Profile/Tunnel Group Only
- Prevent Users from Establishing Remote Access VPN Sessions
The workarounds aren’t possible in all cases. Instructions and more details are available in Thursday’s post. The most effective protection, however, remains strict enforcement of MFA since the requirement will prevent access even when an attacker has possession of the correct username/password combination.


