As identity and access management became a foundational element of cybersecurity, IAM career opportunities have gained more attention. But just what is the IAM role, and what does an IAM professional do? Let’s explore the important skills, qualifications and salaries for careers in identity management, a field that Juniper Research estimated will grow from $16 […]
Microsoft on Tuesday unveiled Zero Day Quest, a bug bounty event offering up to $4 million in rewards to security researchers. The announcement was one of several related to security at this year’s Microsoft Ignite conference, which is being held this week in Chicago. Zero Day Quest, an on-site event taking place next year in […]
Palo Alto Networks warned that attackers are now exploiting two zero-day vulnerabilities in its firewall management interfaces that could let threat actors gain highly privileged access. Last week, Palo Alto Networks disclosed that an unauthenticated remote command execution zero-day vulnerability it tracked as PAN-SA-2024-0015 was under attack. At the time, the vulnerability, which affects PAN-OS […]
The use of biometrics for identity and access management has increased dramatically in recent years, as organizations and individuals seek more secure ways to authenticate who is truly authorized to access apps, systems, data and services. Biometrics enables people to use facial recognition, for example, to unlock their devices or to prove their identity at […]
Motivated by the potential profits of targeting industrial, utilities and manufacturing organizations, threat actors are stepping up their attacks against operational technology companies and their associated assets. In response, OT organizations are racing to create a more effective approach to OT system security from both a technical standpoint and management perspective. One of the major […]
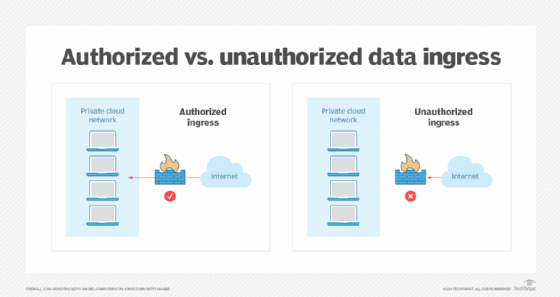
Data egress is when data leaves a closed or private network and is transferred to an external location. This occurs within the context of cloud computing when stored data moves out of a private cloud network and into a public cloud or an external network. The term is commonly used in both network security and […]
It’s no secret that enterprises are operating under threat, with rising risks around network security. As enterprises wrestle with the growing number of threats, they are racing to implement network security management tools and processes designed to keep their operations as secure as possible. Threat actors use a combination of tactics, including phishing, ransomware and […]
A spam trap is an email address that’s used to identify and monitor email spam. It’s also a type of honeypot because it uses a fake email address to bait spammers. Internet service providers (ISPs), antispam organizations, blocklist providers and corporations use spam traps to monitor and reduce the amount of spam traffic to their […]
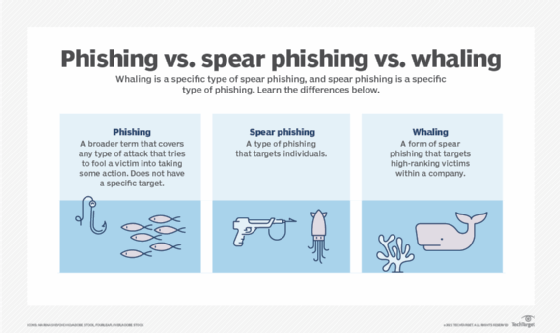
A whaling attack, also known as whaling phishing or a whaling phishing attack, is a specific type of phishing attack that targets high-profile employees, such as the chief executive officer (CEO) or chief financial officer, in order to steal sensitive information from a company. In many whaling phishing attacks, the attacker’s goal is to manipulate […]
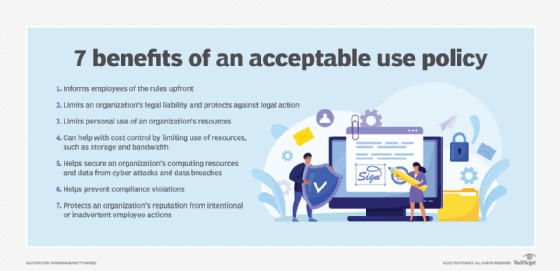
An acceptable use policy (AUP) is a document stipulating constraints and practices that a user must agree to for access to or use of a corporate network, the internet or other computing resources. Many businesses and educational institutions require employees or students to sign an AUP before being granted a network ID. From an IT […]