In early May, hackers infiltrated the Baltimore, Md., computer network. The ransomware attack ended normal business operations, interrupted critical city services, cost the city millions and inconvenienced hundreds of thousands of residents. Baltimore joined the list of other cities that have fallen victim to serious ransomware threats that affect business and commerce. While ransomware attacks […]
The Internet Message Access Protocol, first specified in the 1980s, enables remote users to view and manage messages stored on mail servers. While IMAP has become less important as enterprises and users move to webmail services to manage email directories and messages, it is still widely deployed and used — often behind firewalls and gateways. […]
By Published: 20 Feb 2019 VirusTotal introduced an enterprise version that provides a faster malware search feature and uses N-gram content searches to identify threats. What is an N-gram content search and why is it so important? The practice of identifying threats and sharing information about those threats with defenders was an extension of signature […]
A researcher recently discovered an info-stealer — dubbed Vidar — that is a part of a multi-payload and ongoing malvertising attack that also distributes GandCrab ransomware. How does this double attack work? Who is a target for the attack and how can it be mitigated? Malware infections haven’t changed much over time, even taking into […]
As identity and access management became a foundational element of cybersecurity, IAM career opportunities have gained more attention. But just what is the IAM role, and what does an IAM professional do? Let’s explore the important skills, qualifications and salaries for careers in identity management, a field that Juniper Research estimated will grow from $16 […]
Microsoft on Tuesday unveiled Zero Day Quest, a bug bounty event offering up to $4 million in rewards to security researchers. The announcement was one of several related to security at this year’s Microsoft Ignite conference, which is being held this week in Chicago. Zero Day Quest, an on-site event taking place next year in […]
Palo Alto Networks warned that attackers are now exploiting two zero-day vulnerabilities in its firewall management interfaces that could let threat actors gain highly privileged access. Last week, Palo Alto Networks disclosed that an unauthenticated remote command execution zero-day vulnerability it tracked as PAN-SA-2024-0015 was under attack. At the time, the vulnerability, which affects PAN-OS […]
The use of biometrics for identity and access management has increased dramatically in recent years, as organizations and individuals seek more secure ways to authenticate who is truly authorized to access apps, systems, data and services. Biometrics enables people to use facial recognition, for example, to unlock their devices or to prove their identity at […]
Motivated by the potential profits of targeting industrial, utilities and manufacturing organizations, threat actors are stepping up their attacks against operational technology companies and their associated assets. In response, OT organizations are racing to create a more effective approach to OT system security from both a technical standpoint and management perspective. One of the major […]
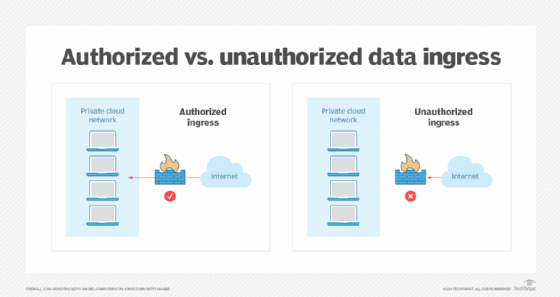
Data egress is when data leaves a closed or private network and is transferred to an external location. This occurs within the context of cloud computing when stored data moves out of a private cloud network and into a public cloud or an external network. The term is commonly used in both network security and […]