The US Department of the Treasury’s Office of Foreign Assets Control (OFAC) on Thursday announced sanctions against two individuals and four entities involved in generating illicit funds for North Korea as part of the fake IT worker scheme. As part of the elaborate operation, North Korean operatives relied on stolen identities and AI to pose […]
President Joe Biden this week issued an executive order aimed at strengthening the United States’ cybersecurity and making it easier to go after hackers. The executive order covers areas such as security in third-party software supply chains, software development, identity, the security of internet protocols, encryption, quantum computing, artificial intelligence, infrastructure and network security, and […]
Vulnerabilities in the SimpleHelp remote access software are trivial to exploit and could allow attackers to compromise the server and client machines, cybersecurity firm Horizon3.ai reports. SimpleHelp provides remote support solutions that include file transfer, diagnostics, and task automation capabilities. It uses clients running on customers’ machines and a server that acts as a web […]
Cisco this week unveiled AI Defense, a new solution designed to help enterprises secure the development and use of AI applications. Cisco AI Defense focuses on two main areas: accessing AI applications, and building and running AI applications. The first is related to the use of third-party AI apps, which can boost productivity, but they […]
Microsoft researchers have uncovered Russian intelligence agencies using spear-phishing tactics to target victims with QR codes and WhatsApp group chats. Redmond’s threat intelligence team documented the discovery Thursday with a warning that the Russian APT — tracked as Star Blizzard — has shifted its longstanding spear-phishing tactics to focus on WhatsApp groups. According to Microsoft, […]
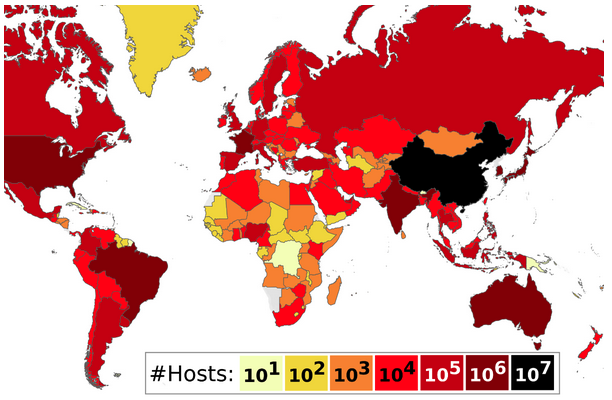
New research shows that over 4 million systems on the internet, including VPN servers and home routers, are vulnerable to attacks due to tunneling protocol vulnerabilities. The research was conducted by Mathy Vanhoef, a professor at the KU Leuven university in Belgium, and PhD student Angelos Beitis, in collaboration with VPN testing company Top10VPN. Vanhoef […]
Authentication solutions startup Wultra on Wednesday announced raising €3 million (~$3.1 million) in seed funding for its post-quantum technology. Tensor Ventures, Elevator Ventures, and J&T Ventures participated in the investment round. Founded in 2014, the Praha, Czech Republic-based startup provides banks and fintech companies with post-quantum authentication that provides secure and seamless access to digital […]
California-based cannabis brand Stiiizy is notifying 380,000 individuals that their personal information was compromised in a data breach at one of its vendors. According to Stiiizy, it discovered the incident in late November, after the vendor notified it of a cyber intrusion, but the attackers had access to compromised systems for roughly a month. “On […]
North Korean hackers are targeting the software supply chain in a new campaign aimed at developers looking for freelance Web3 and cryptocurrency work, cybersecurity firm SecurityScorecard reports. Dubbed Operation 99 and attributed to the infamous Lazarus Group, the campaign represents an upgrade to previously observed Operation Dream Job attacks, luring developers to clone a malicious […]
SecurityWeek’s Cyber Insights 2025 examines expert opinions on the expected evolution of more than a dozen areas of cybersecurity interest over the next 12 months. We spoke to hundreds of individual experts to gain their expert opinions. Here we discuss what to expect with Identities. Identities, both human and machine, occupy a unique position: they […]