600GB of Data and 308 Hrs Deadline Given Post USCS Cyberattack
A ransomware group Knight, formerly called Cyclops has allegedly carried out a cyberattack on US Claims Solutions (USCS). The Cyber Express found no reference to the USCS cyberattack on the website of the insurance firm.
US Claims Solutions is an insurance industry that offers services related to cargo and inspections, commercial loss claims, firearms appraisals, forensic inventories, and more.
The Knight ransomware group exfiltrated over 600GB of data allegedly from the USCS cyberattack.
USCS Cyberattack by Knight Hackers
Knight threatened US Claims Solutions with a deadline of 308 hours and, 2 minutes for the ransom payment. On their dark web portal, Knight wrote that they encrypted the network during the USCS ransomware attack.

With a deadline of close to 12 days for ransom payment from the day of posting, the dark web message regarding the cyberattack on USCS also noted that the management of the firm was given 48 hours to respond to their threat.
The USCS ransomware attack threat was posted on October 17, 2023, and was viewed by 109 users on the dark web.
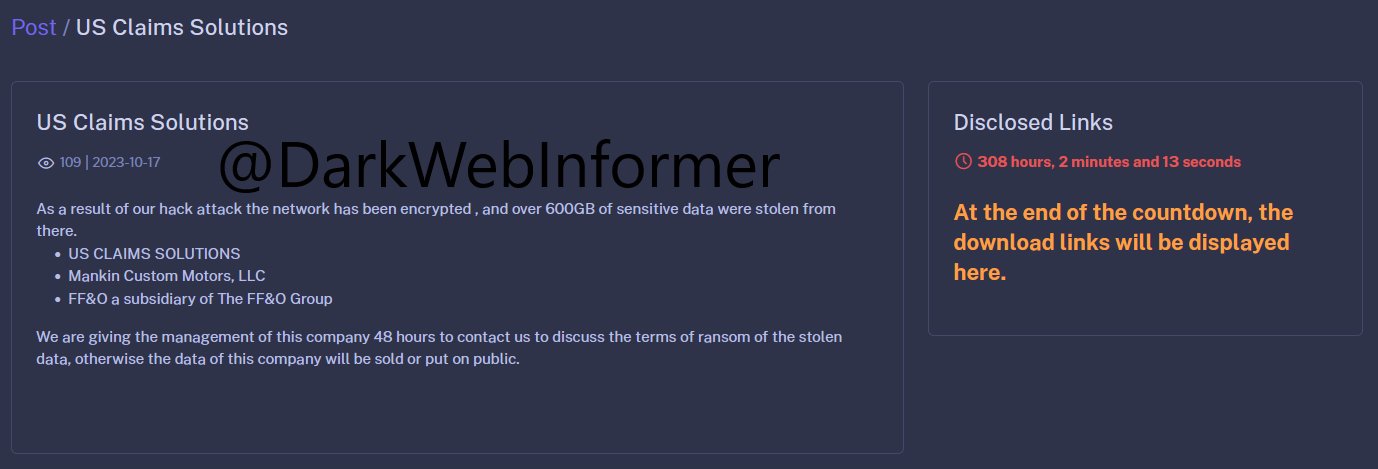
Knight did not mention the information included in the 600GB of sensitive data exfiltrated by them. The deadline of 2 days given to the management of USCS which ends today, was to discuss the terms of ransom. They threatened to sell or publicly release the data exfiltrated from the ransomware attack on USCS if the management would not respond.
“At the end of the countdown, the download links will be displayed here,” concluded the dark web threat by Knight.

Besides the USCS cyberattack, Knight claimed a cyberattack on BMW Munique motors this week.
From Cyclops to Knight Ransomware Group
Cyclops ransomware changed to Knight with the launch of version 2.0 of its Ransomware-as-a-Service operations. The hackers also said that they were recruiting more cybercriminals in their group, back in July 2023.
They seemed to want to make a more distinct identity in the underground world of cybercrime due to which they announced the change and the upgrades to their panel. The members of the Knight ransomware group have been found active since May 2023.
Despite the rebranding and features added to the malicious activities of ransomware groups, legal agencies, and cybersecurity firms have been offering guidelines to prevent ransomware attacks. Mitigation mechanisms include seeking decryption tools to restore encrypted data.
To recover encrypted files, firms can opt for solutions that can decrypt and restore documents placed across storage devices. Several cybersecurity firms offer solutions to access files manipulated during encryption.
However, it is essential to seek professional help instead of doing so following online tutorials that may not be updated or relevant to the attack they faced.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.