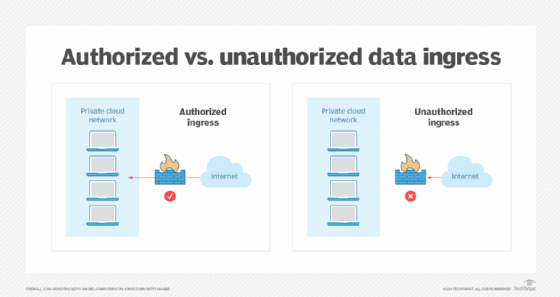
Data egress is when data leaves a closed or private network and is transferred to an external location. This occurs within the context of cloud computing when stored data moves out of a private cloud network and into a public cloud or an external network. The term is commonly used in both network security and […]
It’s no secret that enterprises are operating under threat, with rising risks around network security. As enterprises wrestle with the growing number of threats, they are racing to implement network security management tools and processes designed to keep their operations as secure as possible. Threat actors use a combination of tactics, including phishing, ransomware and […]
A spam trap is an email address that’s used to identify and monitor email spam. It’s also a type of honeypot because it uses a fake email address to bait spammers. Internet service providers (ISPs), antispam organizations, blocklist providers and corporations use spam traps to monitor and reduce the amount of spam traffic to their […]
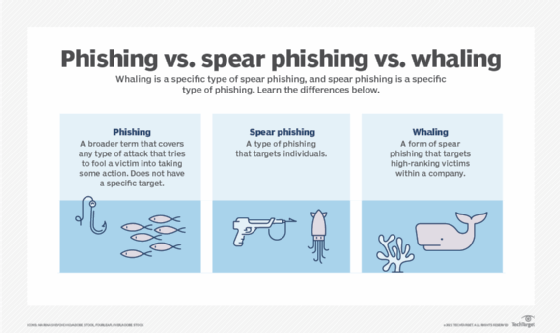
A whaling attack, also known as whaling phishing or a whaling phishing attack, is a specific type of phishing attack that targets high-profile employees, such as the chief executive officer (CEO) or chief financial officer, in order to steal sensitive information from a company. In many whaling phishing attacks, the attacker’s goal is to manipulate […]
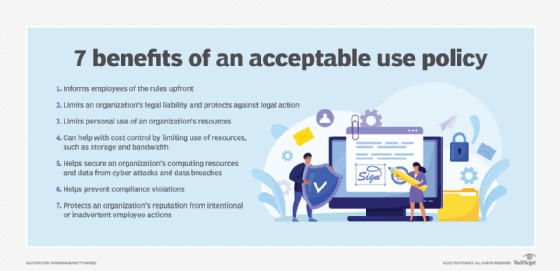
An acceptable use policy (AUP) is a document stipulating constraints and practices that a user must agree to for access to or use of a corporate network, the internet or other computing resources. Many businesses and educational institutions require employees or students to sign an AUP before being granted a network ID. From an IT […]
Amazon will require MFA on member accounts in AWS Organizations beginning in Spring 2025, the company announced Friday. Amazon’s latest announcement comes at the heels of other tech giants similarly announcing expansions of their MFA requirements. Last week, Google Cloud announced it would roll out MFA requirements for all users beginning this month until the […]
Palo Alto Networks confirmed Thursday that a critical zero-day vulnerability in its firewall management interfaces is under exploitation in the wild. The vulnerability, which the vendor tracks as PAN-SA-2024-0015, is an unauthenticated remote command execution vulnerability in PAN-OS firewall software that Palo Alto Networks assigned a 9.3 CVSS score. Word of a potential flaw came […]
Identity governance and administration (IGA) is the collection of processes and practices used to manage user digital identities and their access throughout the enterprise. IGA represents two areas: Identity governance addresses issues of organization, providing practitioners with network visibility, roles, attestation or proof, segregation of duties (SoD), reporting and analytics. Identity administration handles issues of […]
Infoblox warned that threat actors are increasingly exploiting misconfigured DNS name servers to hijack domains using a technique that’s difficult for victims to detect. The network security vendor published a new report Thursday titled “DNS Predators Attack: Vipers and Hawks Hijack Sitting Ducks.” The report expands on an attack vector dubbed “Sitting Ducks” that Infoblox […]
CISA and the FBI confirmed that Chinese nation-state actors have compromised telecommunications provider networks to spy on government and political leaders in what the agencies called a “broad and significant cyber espionage campaign.” The government agencies published a joint statement on Wednesday, which said the U.S. has been investigating the People’s Republic of China targeting […]