DC Health Link’s data breach was caused by a misconfigured server, according to a prepared statement by an executive for the health insurance exchange at a House Oversight Committee hearing on Wednesday. DC Health Link, a health insurance exchange program based in Washington, D.C., confirmed it suffered a data breach last month after a user […]
Securing the U.S. elections may seem solely like a technology challenge on the surface. However, as the November election rapidly approaches and with early voting underway, election security truly boils down to the core fundamental challenge of protecting our nation and maintaining confidence in our democratic processes. Election security is a bipartisan issue and must […]
Security should always be on your mind when online. Whether at a larger organizational level or at an individual level, you should always have at least some way to keep your data safe. And the more data you must protect, the more important the act of data protection becomes. You should be asking yourself how […]
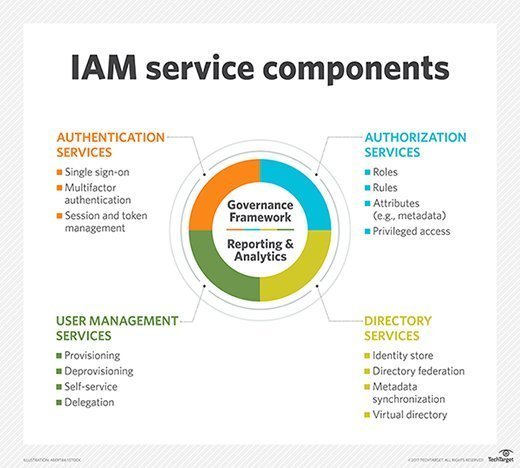
The job market for identity and access management professionals remains strong, but to ace the interview and get the job, you must be prepared for some tough IAM interview questions. Some organizations are looking for IAM analysts to oversee day-to-day operations; others are in a building phase and need IAM engineers and IAM architects. But […]
It’s important to find the silver lining in any negative situation — and this continues to ring true during a global pandemic. As we approach the always-competitive U.S. election in November, politics aside, there is a silver lining there, too. This year, even with COVID-19 concerns increasing the adoption of mail-in voting and chief election […]
The sting of the COVID-19 global pandemic forcing many into remote work — combined with the trend of BYOD in the enterprise — is changing the dynamic of the mobile device convergence. The concept of digital and technological convergence, combining the computing power of a desktop, a smartphone and a tablet into one device, goes […]
A security champions program is critical to maintaining an organization’s security culture, but during the COVID-19 shutdown, teams could find themselves working with one hand tied virtually behind their backs. Telework arrangements, online meetings, collaboration software and extensive smartphone use can keep an organization running, but they can’t recreate the casual interactions that are an […]
There’s a reason why a computer virus is called a “virus,” as they have many similarities to medical viruses. Notably, as medical viruses can have a severe impact on your personal health, a computer virus can severely impact the health of your business. In today’s digital world, a computer virus, a “wormable” remote code execution […]
Having employees connect remotely to your corporate network is not new. Most companies use cloud-based software-as-a-service (SaaS) applications and have some virtual private network (VPN) or remote desktop capabilities to enable field sales staff or roaming users to connect to essential applications and data. However, few — if any — companies were prepared for our […]
What do NVIDIA’s Jensen Huang, Salesforce’s Marc Benioff and Microsoft’s Satya Nadella have in common? They were all deemed the greatest business leaders of 2019, according to Harvard Business Review’s “The CEO 100” list. But another commonality they share is that each have had mentors to help guide them through their careers in technology and […]